The Importance of Cybersecurity


The concept of data leakage has become increasingly more commonplace and the need for protecting your computer is a definite consideration if you don’t want your personal information stolen.
However, cybersecurity is not just limited to personal aspects. It is also a widespread concept for businesses, but not everyone has a comprehensive understanding of what it is, what it includes, and how to apply cybersecurity methods properly.
In this article, we will define cybersecurity and show why it’s important. We will also reveal the benefits of cybersecurity for businesses and discuss the possible types of attacks. Finally, we will offer tips to protect your business from these attacks and how to improve cybersecurity.
What is cybersecurity?
Cybersecurity, in the general sense, is a set of activities aimed at reducing attacks from cybercriminals on digital services, networks, and software. Nowadays, attacks on online businesses have become more frequent, and personal data theft, theft of funds from people’s accounts, or destruction of websites are just a few examples of problems society has faced. Therefore, effective protection from cyberattacks has come to the fore.
What does cybersecurity do? Cybersecurity works on the same principle as traditional security: its goal is to protect users and their digital systems. In the real world, you can install locks, bars on windows, or even alarm systems, but it is not so simple on the internet. Online fraudsters can access your information by different methods. They can even convince you to send them confidential data willingly without realising that you have become a fraud victim. That is why it is necessary to ensure a high level of cybersecurity.
Why is cybersecurity important?
According to the OneLogin report, cybercrime cost the world $6 trillion in 2021. Furthermore, it is estimated that these costs will increase to $10.5 trillion by 2025. These figures speak for themselves.
Many large enterprises such as military, corporate, financial, or governmental organisations store vast amounts of data on computers and other devices. These data include sensitive information that cannot be disclosed to unauthorised users. In addition, businesses often transmit confidential information across networks and devices, and cybersecurity is required to protect this information. With new rules and regulations (e.g. GDPR), companies of all sizes need to consider their staff and clients’ personal data.
That is why companies should take appropriate steps to make sure that access to all sensitive information is restricted to unauthorised users. It is worth noting that cyberattacks have become a top threat to national security today. So the importance of cybersecurity is evident.
If you feel you need to ensure that your software is secure enough, contact us so that we can analyse it and consult you on better protection.
How your business can benefit from cybersecurity integration
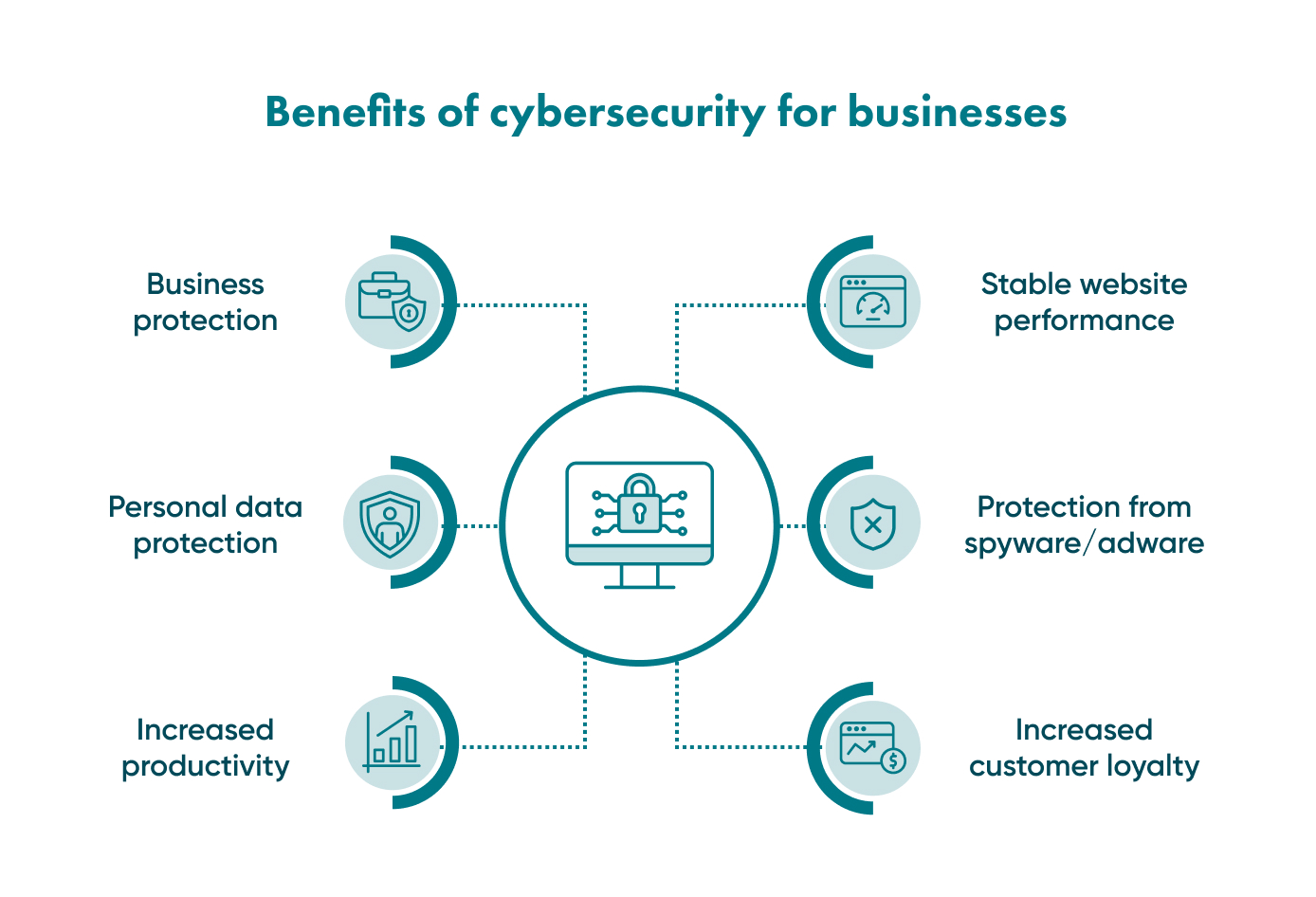
There are several business cybersecurity benefits as follows:
Business protection
First, of course, you can protect your whole business and avoid financial losses. Digital security will provide you and your customers with a comfortable working environment. It means that your website or mobile app is appropriately protected from cyberthreats.
Personal data protection
There are many types of malware intended to steal personal information and sell it. Anti-viruses and firewalls will help protect customers’ data from potential theft.
Increased productivity
Digital viruses and worms can significantly slow down the internal network performance and performance of each computer in particular. Cybersecurity precautions can help to take care of it, and you will have protection from online attacks.
Stable website performance
If there are massive attacks on your website, the chances are that it will crash and stop functioning. This creates problems both for you and your customers. Cybersecurity measures aim to make your website prepared for all potential attacks and defeat them.
No chance for spyware
Spyware is a type of malware that infects your computer and relays all data to cybercriminals. This is specifically run in the background so you won’t even know about it as it doesn’t impact the computer’s performance. An appropriate firewall will build a reliable digital wall against such malicious threats.
Adware isn't welcome either
Online advertising is not a big deal, but you will agree that it may be annoying, especially when it pops up every minute and distracts your attention. Special ad blockers will help you get rid of aggressive marketing campaigns and focus on your responsibilities.
Increased customer loyalty
When your customers know that your website or mobile app is secure enough and their data is adequately protected, they will become more loyal to your services and trust you more.
What is cybersecurity risk?

It is crucial to know your enemy and understand their methods. For this reason, we list the most common cyberthreats that never sleep and can attack your software at the worst possible time. This should help you understand why cybersecurity matters.
Malware
This term includes different types of threats referred to as viruses such as trojans, which are used to control your helpful software, and worms used to delete files and reduce a device’s performance. Ransomware is another form of virus that blocks your data, and attackers extort money to unblock it, or they delete it or make it public. Spyware is the infamous malicious software that intrudes on your device, works in the background, and steals sensitive data from it.
Phishing
Its name is similar to fishing because cybercriminals take some illegal steps to catch users and make them share valuable information to steal their funds or credentials. Usually, phishing attacks are performed via emails where users are recommended to click the link and enter their credentials. Then, criminals can access your banking account, for example, and clean it out. Apart from online phishing, voice phishing or vishing (via phone calls) and SMS phishing are also possible.
MitM attacks
MitM stands for Man-in-the-Middle. It refers to the situation when criminals intercept the message between two users and replace it, without users knowing that there is someone in the middle. Thus, attackers can intercept and completely change the text and convince users to share a piece of sensitive information.
DDoS attacks
Distributed Denial of Service (DDoS) attacks include a massive attack which can shut down your website (remember?) or your central server with multiple data requests within a short period. When the system is not prepared, it will be shut down because it cannot process so many requests at once.
SQL injections
This type of attack is prevalent among cybercriminals, and it implies inserting malicious code into a server using a Server Query Language (SQL). SQL connects servers to a database. SQL injection means that a random code is inserted into the server, and criminals gain complete control over your website.
XSS attack
XSS stands for cross-site scripting, and it is an attack on web systems when malicious code is integrated into a specific website’s page. This code interacts with remote servers of criminals when a user opens this page. As a rule, this is a reliable website, and users don’t even know that criminals use their credentials.
Rootkits
Rootkits are installed inside standard software, and they provide administration-level access to a system. Cyberattackers can use rootkits to control software or a whole operating system and get all sensitive information like passwords, logins, payment card data, etc.
Contact Go Wombat to build your software with high-level protection — we offer cybersecurity consulting services!
Steps to protect your business from cybersecurity attacks
Attackers do their dirty job 24/7, but cybersecurity specialists are always alert as well. So, we have prepared some crucial insights into reliably protecting your software. This is how cybersecurity works.
Update your software
Unfortunately, sometimes hackers may find vulnerabilities in software faster than developers can locate them and create methods to protect it. That is why it is necessary to install all new updates as quickly as possible. We recommend you turn on automatic updates for each device, automate security updates for the browser, and also make sure that you update all plugins in your browser regularly.
Use antiviruses and firewalls
Reliable antiviruses will be the best solution to defend your computer or mobile device from malware. It is important to find out which antivirus provider is the best available on the market, and which one fits your demands better. Also, don’t forget that your device must have only ONE antivirus software installed.
As for firewalls, they create a wall between your device and the external digital world, and they filter all malicious information that tries to access your device.
Set strong passwords
Passwords like “1111” or your birth date are far from being strong passwords, as these can be easily guessed. Therefore, make sure that your password contains both small and capital letters, numbers, and symbols — it is a challenge for criminals to crack this type of password. You can even use password generators to help you create a strong password. Another strong form of a password is a phrase, for example, “I love peanut butter for breakfast” which is more complicated to predict.
Opt for multifactor authentication
Today, two-factor authentication is the most widespread authorisation method. When you enter your login and password, you need to confirm your identity via the phone or biometrics (fingerprint scanning, face recognition). Multifactor authentication adds more authorisation methods to those mentioned above, and we consider this authentication to be the most secure.
Be suspicious
Why is it impossible to eliminate phishing attacks? Unfortunately, many people are still too susceptible, and they don’t even know that criminals create phishing emails for fraudulent purposes. Therefore, don’t open emails from unknown addresses. Don’t click any link until you make sure that it directs you to the right website.
All trustworthy email providers usually have a scanning system to identify suspicious emails. The main takeaway is to remain vigilant!
Be careful about PII disclosure
Personal Identifiable Information (PII) includes your name, address, age, date of birth, location details, social security number, etc. Unfortunately, with so many people using social media today, it is much easier for cyberattackers to identify all of the victims’ information. So don’t show all your personal information on social media, and review your privacy settings to protect your personal account.
Backup your data
Never store all your data on one device. There should be at least three copies, both on different devices and in cloud storage. The best way is to set up an automatic backup in your messengers and other services to copy your data regularly.
Be wary of free public Wi-Fi
It doesn’t mean you shouldn’t use it at all. You just need to use Virtual Private Network (VPN) to encrypt the traffic. When you use Wi-Fi at home, set a password to protect the network from unauthorised access.
Unlock Success with Premium Software Development
Contact us


How we adhere to cybersecurity at Go Wombat
At Go Wombat, we pay strict and careful attention to the software security level our company creates, which is why we have a certified Chief Security Officer (CSO) specialising in and responsible for cybersecurity. The specialist monitors the compliance of developed software with necessary regulations and security standards, tests it for vulnerabilities, and applies up-to-date techniques to protect the software.
Go Wombat understands the importance of cybersecurity, and places it at the forefront of any project discussions. This is partly how we have carved out a reputation as an expert software development company. To ensure Go Wombat’s continued expert cybersecurity coverage, our CSO is continually upgrading his knowledge and certifications. This ensures we are always in tune with the latest threats and developments.
When thinking about the development of your software with all required security integrations, you can rest assured we will take care of it. Furthermore, we will also explain how to invest in cybersecurity wisely.
Go Wombat is looking forward to your requests — we are always glad to work on a new project. Contact us!
How can we help you ?






