Cloud Data Security: Guidelines to Ensure Strong Protection of Sensitive Data in Cloud Environments


When organisations move their corporate data to the cloud, it provides them with multiple benefits like seamless access, synchronisation, and cost-efficiency.
However, it is vital to make sure that your cloud environment is protected against malware and unauthorised access, especially when employees are working remotely.
Cloud data security is one of the most important factors when evaluating the best way to perform a company-wide digital transformation. High security and control levels are a must, and proper cloud storage carried out with a reputable web developer with experience is essential.
In this article, we will go over the definition of cloud security and review the existing setups for cloud environments. We will also discuss the importance of protecting your cloud network and provide steps to ensure a secure remote network.
What does cloud data security mean?
Cloud data security is a broad term that encompasses all technologies and recommendations for improving data protection in a cloud environment.
In short, cloud application security ensures confidentiality and protection of information stored in your organisation’s cloud, as well as its compliance with regulatory requirements.
Cloud data security is essential at all times. Whoever, it’s particularly important during a data migration project. In this case, there needs to be a close adherence and clear understanding of GDPR issues.
The term also includes optimised security management tools and processes that increase the reliability of a system, notify about potential threats, and identify incidents.
To ensure cloud security, it is necessary to develop a business continuity strategy and a backup plan in case of any emergency, like a data breach.
With all that said, it’s also important to note that the best cybersecurity solutions also depend on the type of cloud environment.
Types of cloud environments
Within the realm of cloud data security, there are three environments: private, public, and hybrid.
We will review each of them separately.
Private cloud
It is a cloud infrastructure that belongs to a single company or organisation.
Entities with a private cloud don’t share physical or virtual resources with others. All of the data stores, server space, and other assets belong to the company.
Public cloud
Public clouds are available to any individual, organisation, and company, as long as they pay the price set forth by the service provider.
The virtual IT infrastructure of the cloud service belongs to the provider, and the provider rents it to companies. The 'public cloud' is also known as IaaS — infrastructure-as-a-Service.
The service provider allocates a required pool of virtual resources to the client, so the client pays for a specific cloud volume.
In most cases, public clouds were private clouds until their owners accumulated enough expertise in cloud management to commercialise their experience.
Hybrid cloud
This is a combination of private and public: part of the infrastructure is in the provider’s public cloud and the other part in your company’s private cloud.
Additionally, hybrid clouds also include setups where the organisation stores data locally as well as on public clouds.
This setup can vary tremendously, so it’s best to partner with an experienced IT professional to establish the right infrastructure.
What type of cloud solution would suit your company’s infrastructure? Go Wombat will provide a detailed answer during our consultation. contact us
Why cloud data security is important for your business
The importance of cloud security for your business cannot be understated, but apart from protection from threats, it also provides other advantages you should certainly know about.
With new technologies becoming more ubiquitous, such as progressive web applications (PWA), data security is an ever-present issue.
Let’s look at some of the benefits of a strong cloud cybersecurity system.
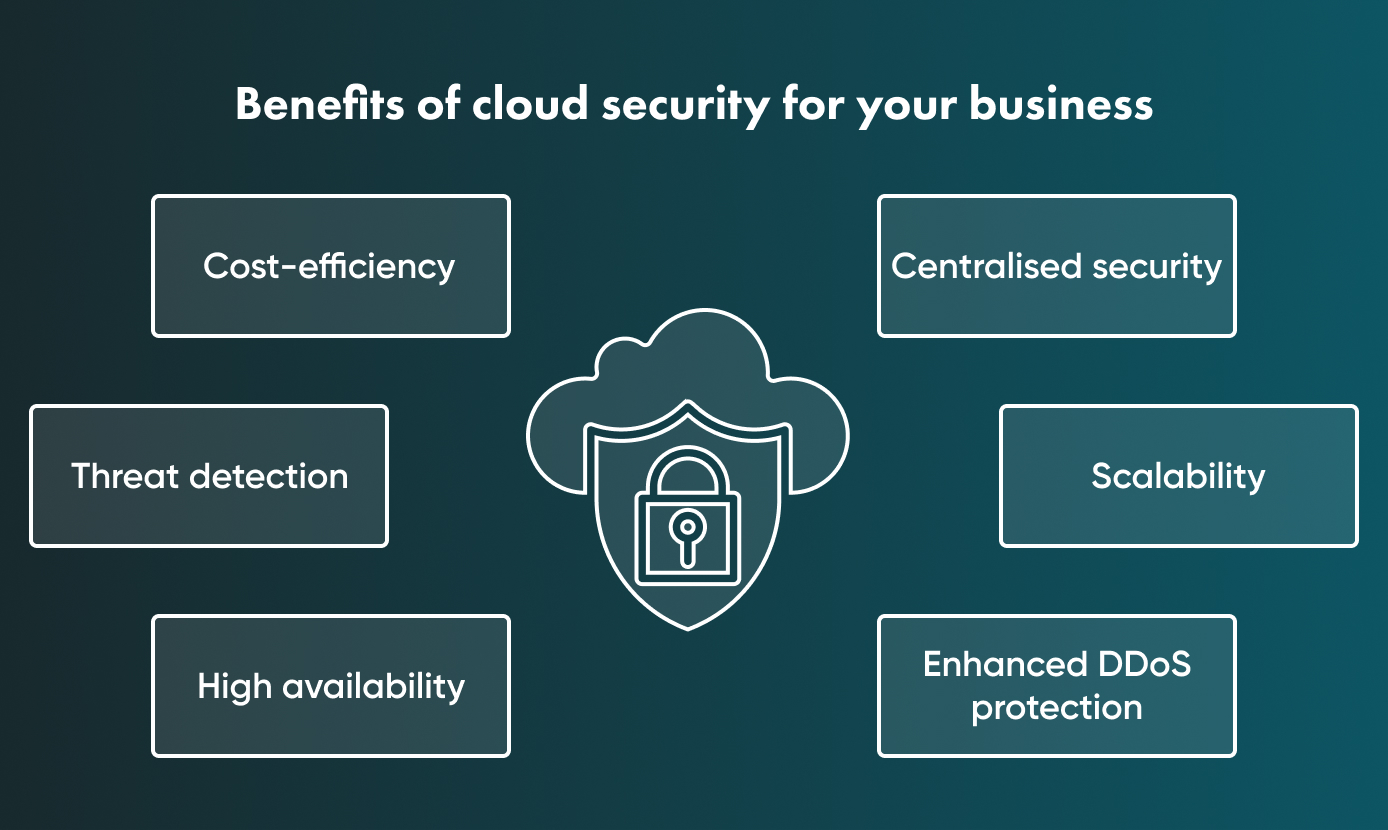
Why cloud data security is important for your business
The importance of cloud security for your business cannot be understated, but apart from protection from threats, it also provides other advantages you should certainly know about.
With new technologies becoming more ubiquitous, such as progressive web applications (PWA), data security is an ever-present issue.
Let’s look at some of the benefits of a strong cloud cybersecurity system.
Cost-efficiency
First, you don’t need to purchase hardware and hire a team to set up a strong security mechanism from scratch.
The cloud service provider will maintain everything, and you can easily use your cloud environment.
Also, you can lower administrative expenses, and the service provider will deal with any security issues.
However, all configurations and maintenance are in your hands if you use a private cloud.
Threat detection
Reliable cloud service providers apply scanning techniques to detect threats as soon as they are apparent.
Endpoint scanning, for example, is one of these effective detection techniques. It implies scanning devices that connect to your network before granting them access to ensure that the connection is protected at all times.
High availability
Cloud data security ensures that access to your remote data occurs over a safe connection.
It ensures that your essential data is always available to you, your employees, and your clients (if you provide some cloud-based solutions for them) from any point in the world.
Providers that don’t pay careful attention to cloud security will be at a clear disadvantage. Therefore, it is better to get help from a professional team in not only setting up your cloud environment, but your entire security system as well.
Centralised security
With cloud computing, you get a centralised location for your information and applications. When set up correctly, cloud computing solutions also bolster the safety levels of everything you store there.
It also simplifies the vulnerability scanning process by the cloud provider, since all information is in a single place.
Scalability
Cloud environments are powerful enough to support large corporations, which makes these networks inherently scalable. Same goes for the security systems that can be designed for them.
Whenever you need to add more information or extend the capabilities of your software, the cloud platform will scale according to your demands without affecting data safety.
Enhanced DDoS protection
Finally, distributed denial of service, or DDoS attack, can decrease the performance of your website or even crash it. This, in turn, can leave your website or app vulnerable to additional attacks.
Cloud security provides comprehensive DDoS protection that will enable your software to function uninterrupted, even under extreme circumstances.
Key elements of a secure cloud protection
How does cloud security work?
When looking for a dependable solution, you need to consider several aspects of a cloud service provider.
Let’s take a look at some of the key aspects you should keep in mind when choosing your cloud provider.
Security controls
Pay attention to built-in security controls that help you prevent data theft, unauthorised access, data leakage, and other threats when choosing your cloud provider.
Authentication
Your service provider should offer multi-factor authentication to minimise the chances of suffering a breach and losing access to your information.
It’s also a good idea to find a cloud service provider that offers a single sign-on. This will allow employees and other stakeholders to connect once and access your platform without having to log in again.
Encryption
All data on your cloud storage should be encrypted. Better yet, aim to only work with cloud providers that have zero-knowledge encryption.
Simply put, this type of encryption is that even service providers cannot access data you store on their platform.
Remember that your data must be encrypted at rest, in use, or in transit.
At rest means inactive data. In-transit data means data that is transferred from one point to another. In-use data means data that is read, processed, or changed continually.
In-depth analysis
Pay attention to cloud service providers that use machine learning solutions to predict potential attacks, and detect unwanted criminal activities at early stages.
Some cloud platforms may even provide data behaviour analysis, which helps identify suspicious activity from your employees.
Compliance
You may also want to verify that the cloud setup is GDPR compliant. As a matter of fact, you should verify that your service provider continuously complies with all regional, industry, and additional relevant regulations, like CCPA, HIPAA, FINRA, and so on.
This will help you avoid legal issues and provide better overall service. Also the time to review your own security system to ensure it abides by all requirements set forth in these regulations.
Compatibility
Finally, it is necessary to make sure that the security solutions of a cloud provider are compatible with all your applications, and they can control the security of your software without affecting the customer experience and functionality.
The team of Go Wombat is always ready to build a cloud-based solution that takes all of your security requirements in mind.
Contact us to book some time with our cloud security experts.
Remote work: best cybersecurity practices for business owners
Even if you use a reputable cloud service provider, it doesn’t mean that cybercriminals cannot attack you or your employees.
If everyone works remotely, you can’t assume the safety of all confidential business information.
To help you out, we want to share a few tips to build a more robust cloud security system.

Migrate your business apps to the cloud
All business apps that are compatible should be moved to the cloud, along with any other necessary data and sensitive pieces of information.
Your business apps and other data should be encrypted and stored in the most secure way possible.
Create a remote work policy
Writing a remote work policy will help reduce security issues and set clear expectations for your team members.
In addition to best practices that remote workers have to follow, this can also include tips to help keep your cloud environment safe.
For example, your policy can include compliance requirements, data protection tips, backup plans, and remote access control protocols.
If you don’t even know what a remote working policy should comprise, let Go Wombat assist you — our Chief Security Officer (CSO) will draw up a detailed plan describing all security loopholes you need to consider, as a certified cloud security professional.
Promote the use of password managers
A great way to set a high security standard is to require employees to use a password manager to create a reliable password. Additionally, also encourage team members to take measures to protect their credentials, like avoiding sharing them with anyone.
Train your employees
Never assume that your employees are familiar with security best practices.
Instead, take it upon yourself to train your employees on effective security habits and best practices. By providing thorough guidelines, you’ll be able to teach your employees how to stay safe and how to react if they identify a potential breach.
Also, you must require employees to connect to VPNs and use multi-factor authentication on all company tools.
We have covered these tips in our article about cybersecurity - an essential read for those who want the nitty gritty details.
In addition, here are some recommendations for employees:
Use company’s devices for business-related tasks only
If your company provides any gadgets or equipment, it’s imperative that your team members only use it for tasks related to your organisation.
Not only this, but these devices should have security software installed, integrated protection techniques, and cloud security certification. It must be updated regularly in order to protect the user from all known and future cyber threats.
However, if your company adheres to the BYOD trend (Bring Your Own Device), then remember to promote the use of VPNs, antivirus software, and firewalls so that you can ensure a smooth and flawless working process.
Make sure that all employees adhere to the company cloud service
It is crucial for all employees to use cloud services approved by your organisation. This will help ensure that all team members are adhering to the same security standard.
Avoid sharing sensitive information via email
Emails will not provide the same encryption level as cloud services.
When you send a file by email, it is transmitted in a non-encrypted format, so there’s a higher chance of the information being hijacked or used.
Therefore, it’s always best to share your sensitive information via cloud services where the encryption level is high.
Unlock Success with Premium Software Development
Contact us


Conclusion
Run updates regularly, don’t open emails from unknown sources, secure video meetings, and always stay alert. These are some of the golden rules your team should follow to maintain good cloud security levels.
Cloud security will only work if you adhere to all security guidelines.
At Go Wombat, we emphasise security in the software we create.
Our chief security officer monitors the integration of all security standards into clients’ projects since we are responsible for the result – this is a usual standard in our organisation.
If you need to build a cloud-based app and want to get help setting up its security, our specialists can help by following up-to-date regulations.
To learn more about getting help setting up your cloud data security, contact Go Wombat today and our team will be glad to help.
How can we help you ?








