Continuous Security Monitoring (CSM)


What is it and how can your business benefit from it?
Businesses are constantly needing to adapt to new conditions. One of these conditions and their changes is theft and loss of data. In 2022, the healthcare sector will be the leader in the cost of data loss with a US$ 10m average payout. The truth is that many of these difficulties could be avoided.
Depending on the industry and the size of the company, the damages from data loss can vary. But one thing that is evident in the digital age is the loss of corporate data can devastate your reputation, reduce your company's investment appeal, and lead to customer churn.
Fortunately, a responsible approach to cyber security and awareness of how to protect data is an excellent preventive measure. And this article is meant to inform you about the purpose and benefits of CSM.
Go Wombat can share our experience with you to achieve the best result. To discover how CSM can help your business, give us a call today.
What Is Continuous Security Monitoring (CSM)?
In simple words, Continuous Security Monitoring is a protective system that should track possible damages to sensitive data within IT infrastructure.
Even a world-class information security policy can't give you a 100% guarantee of a leak-proof system and risk management without mistakes. CSM helps to determine possible damages before they affect the security of sensitive data.
Traditional security applications and software, such as firewalls, antivirus software, and penetration testing, are insufficient to prevent most attacks by hackers.
With Common Vulnerabilities and Exposures, (CVE) databases receive more and more new attacks exposing new vulnerabilities every day, even if your infrastructure is reasonably secure.
There are four main risks to IT infrastructure's cybersecurity. It's vendors, rogue assets, and known and unknown assets. Each of them has different ways to gain unauthorised access to corporate data.
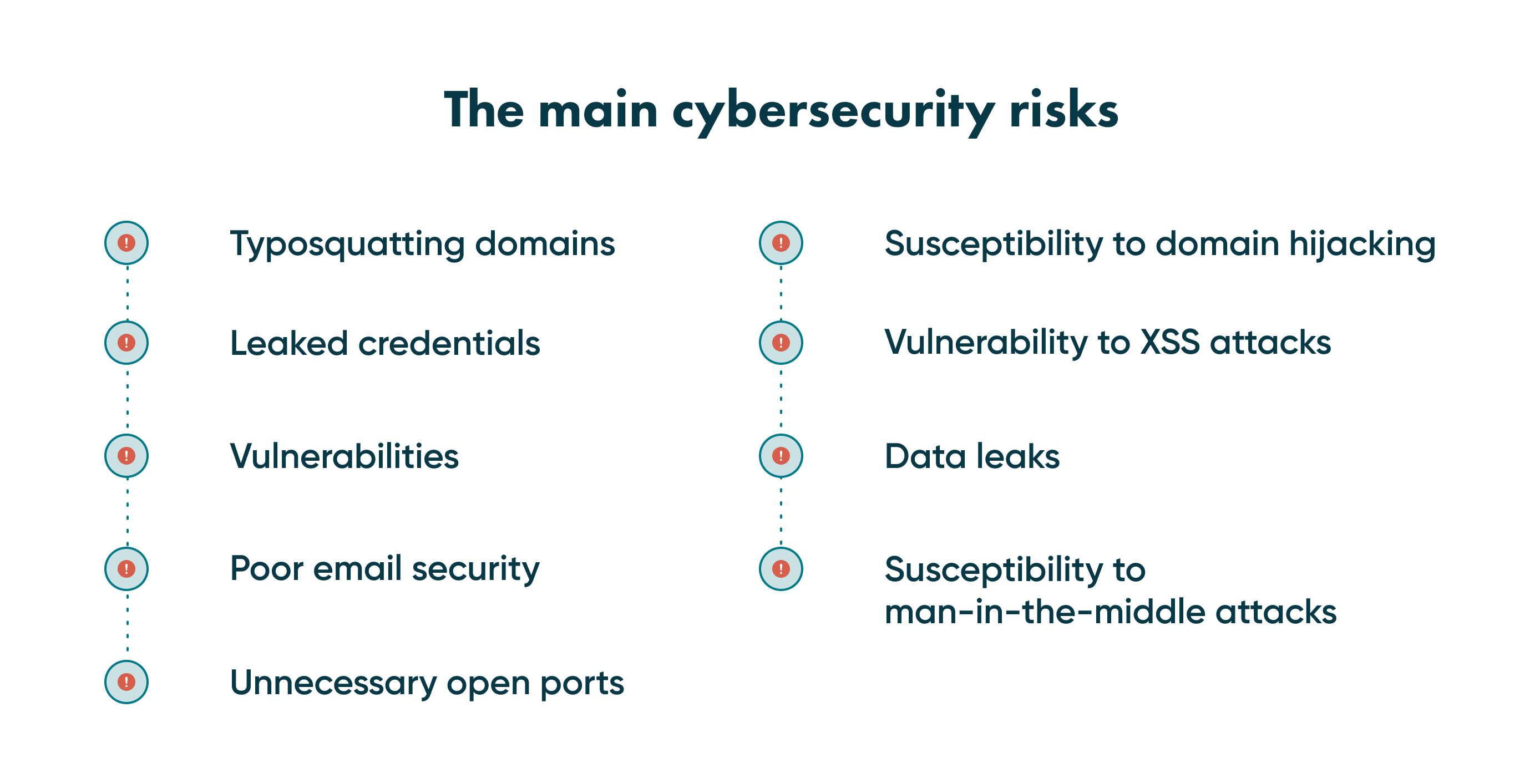
The thing that connects them is why they have a chance to infiltrate into a secured system. In most data breaches, it's a human error factor and the inability to cover all the potential entries of harmful software.
Why is continuous monitoring an important element of security?
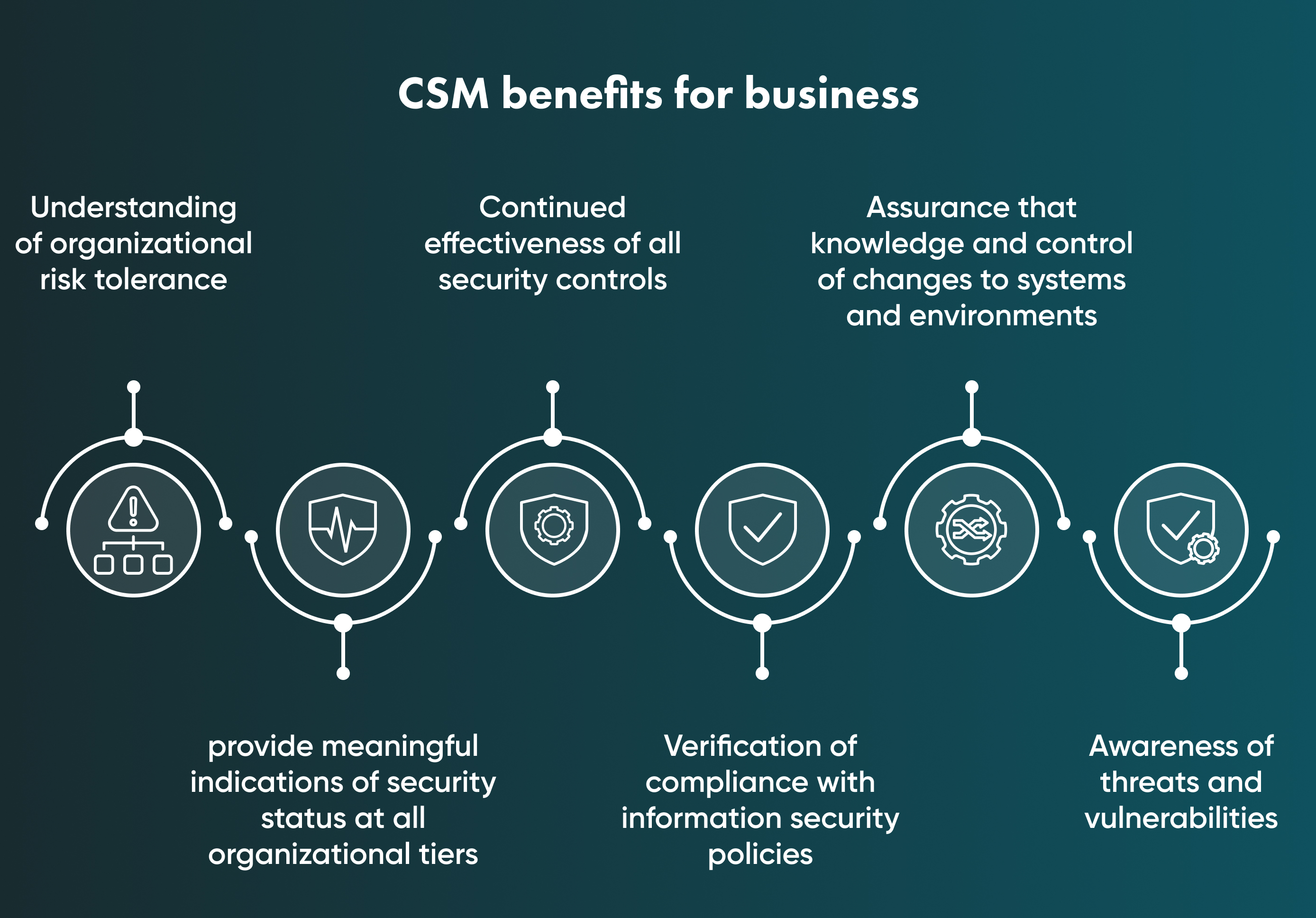
Ensure Compliance
Criminals are constantly looking for weaknesses to take advantage of. Workloads on the cloud are frequently their target. Once more, continuous security monitoring is both helpful and essential in this situation.
With the speed and scale the cloud structure offers, workloads operate for a short time only. No matter how briefly your workload is spun up, you need constant monitoring to make sure that vulnerabilities are identified to stop bad actors from getting a foothold in your environment.
The increasing digitization of sensitive data laws
CSM is important for organisations all around the world, that are responsible for storing the digital data of their clients. The top priority is customer personally identifiable information (PII) or employee-protected health information (PHI).
24/7 protection
The privilege of using software tools to cover business needs is the ability to use these tools any time you need them. CSM doesn't need rest, weekends, or breaks like any other digital service. This feature makes this system a constant protector of cybersecurity vulnerabilities.
Discover Security Risks
Real-time visibility into your whole cloud infrastructure is provided by CSM. With complete visibility, security teams may more quickly identify, address, and eliminate both person and non-person-based issues, such as unauthorised access to data, misconfigured cloud controls, and excessive permissions. In other words, teams can use the important insights provided by CSM, such as indicators of exploitation, to quickly resolve problems.
Increase Visibility and Transparency of a Network
The goal of continuous monitoring of security is to increase accountability and visibility of network activity, particularly suspicious network activity that could indicate a security breach, and to lower the risk of cyber-attacks through early warning systems (EWS) that trigger quick responses. Software for CSM is used by enterprises.
How Does Continuous Security Monitoring Work?
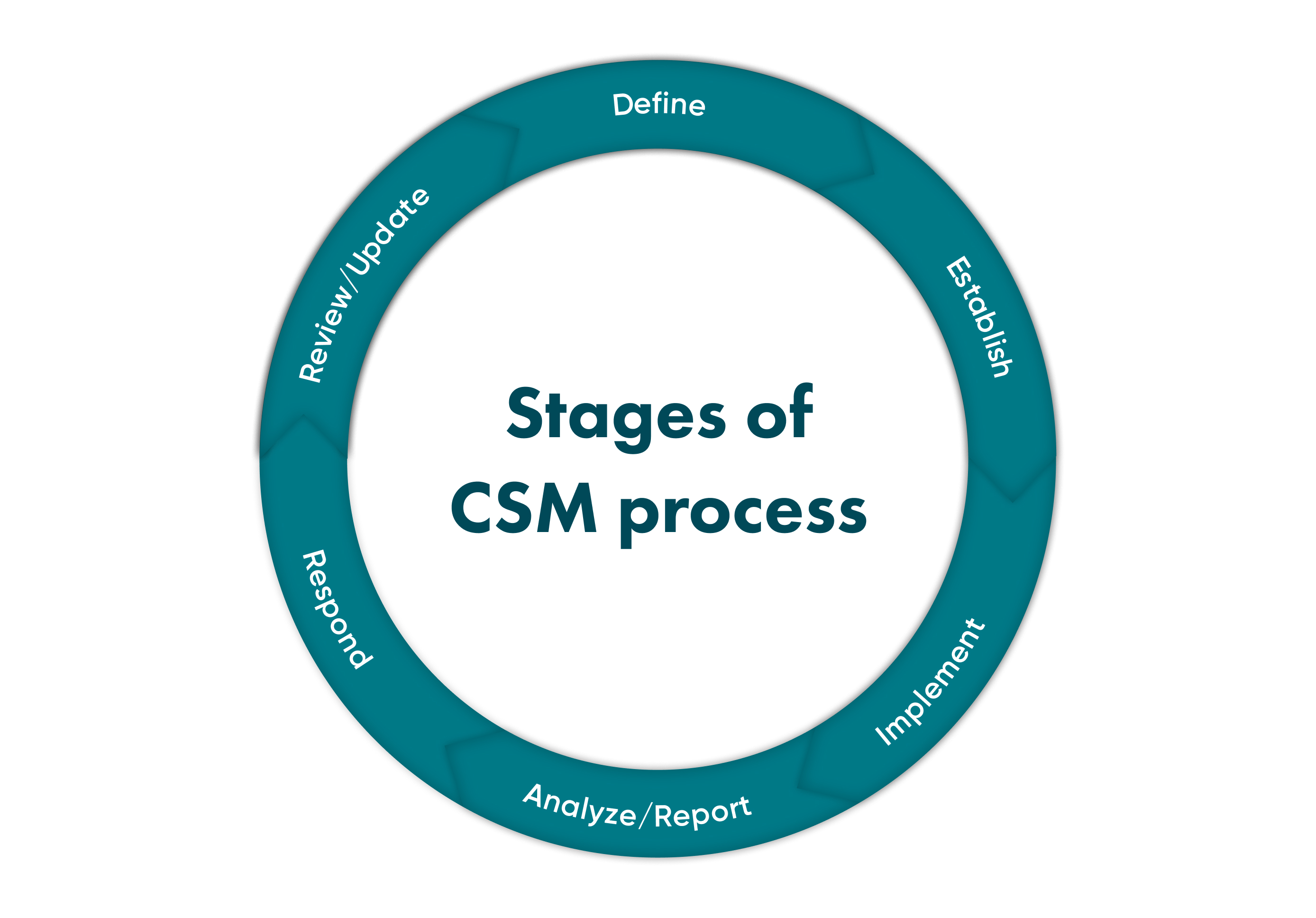
CSM works according to international cybersecurity standards and rules. According to white papers of the National Institute of Standards and Technology, CSM, also known as information security continuous monitoring work, is led by the following rules:
-
Risk management frameworks and information security are integrated.
-
Situational awareness has to be maintained for both organisation's IT ecosystem and vendor system.
-
Setting the need to understand the threats and threat activities.
-
Security control assessment.
-
Security-related information should be collected, correlated, and analysed.
-
Setting clear communication about security status between all departments.
-
Company's top management should provide active risk management.
Read more about risk management in our previous article on the cybersecurity cycle.
What can CSM track?
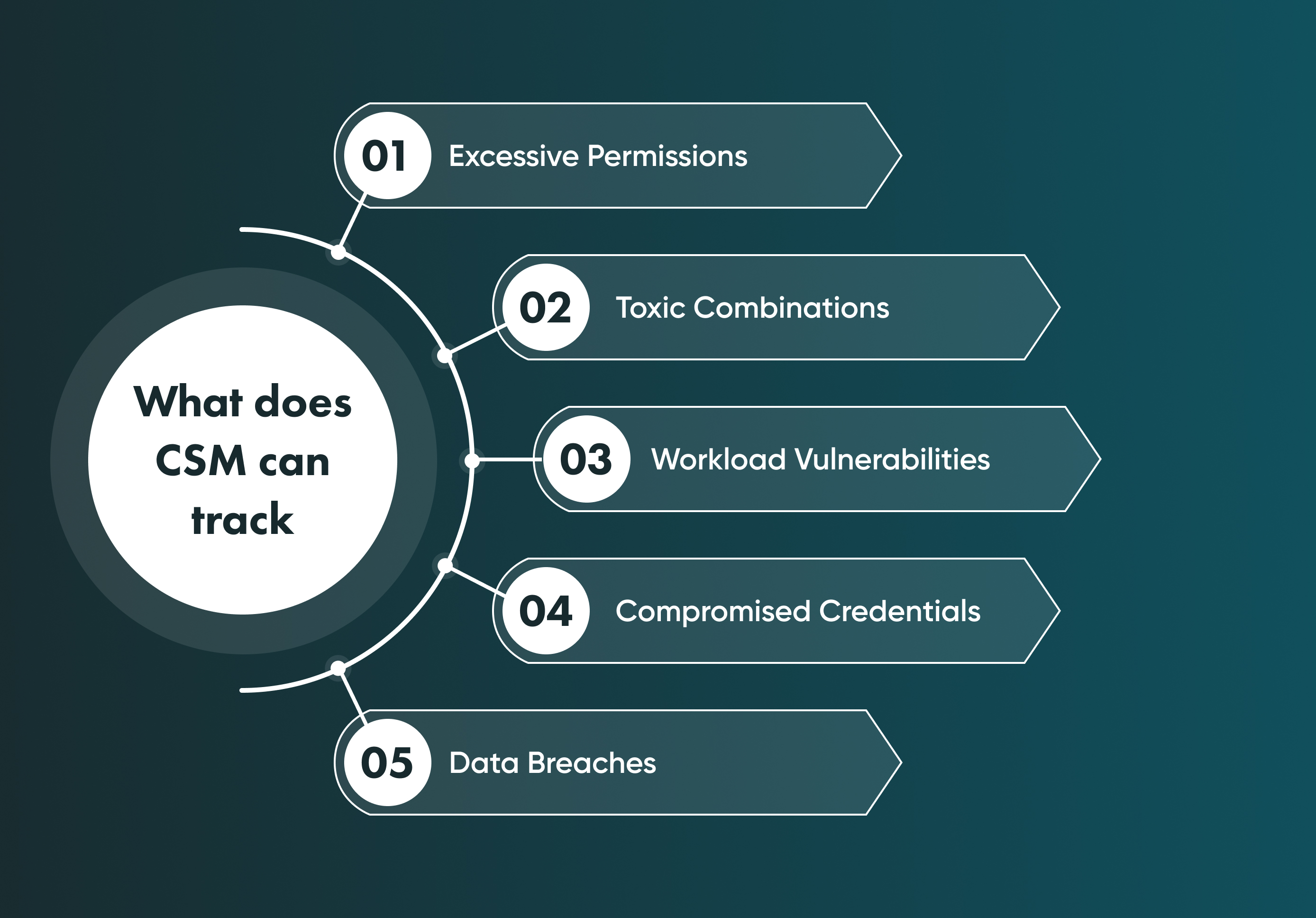
Excessive Permissions
The permission you give the software to use your device or data may have side effects. For example, installed apps have to collect some data to provide users with the service those apps are created for. However, this is the place where the big problem of modern cybersecurity hides.
Some apps and software have unnecessary permissions to use the data they don't need. So, understanding given permissions are essential to prevent data stealing and installing harmful software.
Toxic Combinations
Tracking and detecting the toxic combinations of your network and IT infrastructure takes two of the most limited resources, attention and time. Meanwhile, toxic combinations are dangerous cases with an unpredictable scale of side effects for business.
For example, a toxic combination of privileges to access within the company leads to conflictive decisions. CSM tools can track and prevent those cases.
Compromised Credentials
Credential compromise can frequently result from sharing credentials, using weak passwords, or other malicious methods. Unauthorised users may therefore obtain access to confidential information or utilise their environment's privileges.
This atypical identity behaviour would be picked up by CSM, which would also notify you of any suspicious activity. This may enable you to prevent a breach from occurring.
Data Breaches
It can be difficult for businesses to track data across several cloud settings. It can be simple to lose track of data or overlook a data leak without real-time visibility into data mobility. You can track every data transfer and identify whether it has been moved somewhere it shouldn't be with the right technology and security monitoring that provides real-time visibility.
How to implement Continuous Security Monitoring?
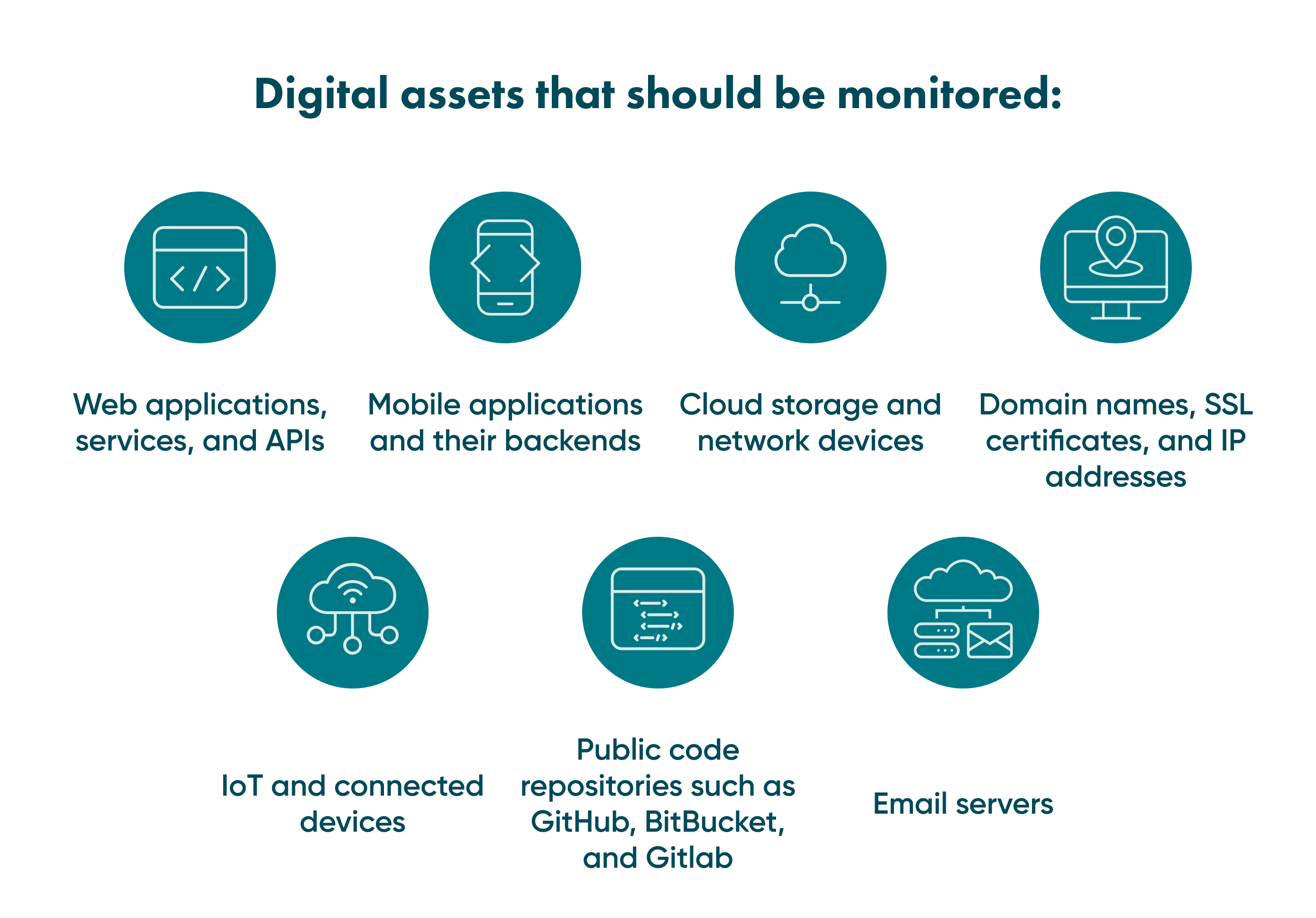
Identify your data
Analyse the weaknesses of your data, including the possible ways of leaks. Then, find which data types are the most sensitive and need to be monitored first.
Pay close attention to both external and internal ways of losing data. The excellent strategy predicts possible acts from cybercriminals and internal bad actors within your company. For example, weak knowledge of essential cybersecurity of one key employee with access to critical data can lead to a major leak.
Identify your users' behaviour
As mentioned above, an internal danger to data is real. Mainly the internal damage is caused by ignorance, but sometimes companies face stealing and selling data to third parties by people from inside.
It happens when employees' access to different levels of vulnerable information isn't checked, monitored, and customised. Your security depends on your daily choices and monitoring strategy.
Set a strong auto-discovery process
There are multiple possibilities and instruments for making routine manual tasks more effective. Plus, it cuts the human error factor to the bare minimum. Tools like AI, your attack-detecting software, and web crawling help us quickly detect any possible cybersecurity danger of your network before they cause data leaks. So, malicious software from unknown IP addresses is no longer an unpredictable danger.
Keep a track of your endpoints
This stage is an example of best practices for CSM and is essential for finding and preventing cyber attacks. Therefore, the target objects for monitoring are endpoints and all the devices in use.
Unlock Success with Premium Software Development
Contact us


Conclusion
CSM is a risk-detecting strategy that provides your business with constant security controls and tracking of potential dangers. The main benefit of setting up CSM has the opportunity to be one step further and eliminate system vulnerabilities before cybercriminals can use them. As a result, the company can set a robust prevention strategy and reduce the number of potential data leaks.
As CSM enables businesses to continuously examine their overall security architecture, CSM is crucial for ensuring that they are adhering to their internal information security policies both on a daily basis and whenever changes take place.
As long as there are instruments for damaging software and stealing personal data, we need to create and improve new ways and tools for protecting your network. CSM is required as long as we use software and hardware with possible issues and vulnerabilities.
Creating and setting up CSM needs a qualified team of developers, software testers, and other specialists. You can find the people to bring your ideas to life in Go Wombat. Contact us for more details.
How can we help you ?






