The Importance of Cybersecurity for SMEs


What makes SMEs targets and what are the risks from hackers?
We hear about a large company’s data loss or a breach every few months. This can create an illusion of data safety for small and medium businesses. You are safe from cyberattacks or data breaches if you don't have such an amount of data as the company with more staff or customers, right?
We need to look at the latest statistics. According to the Verizon Data Breach Investigations Report, as many as 43% of all breaches occurred in small businesses.
So, an equally high number of small businesses are at risk of attacks. One of the reasons hackers target SMEs is a lack of cybersecurity awareness. In the short-term strategy, a tight security budget can save you some money, but in the long-term, not investing in data or cybersecurity for your SME is a risk that could lead to significant financial losses.
You can get all the needed information about how to start your SME cybersecurity awareness from this article. A detailed assessment of your GDPR or security needs will be made evident through the Project Discovery Phase. If you have any questions, ask Go Wombat, and we will help you to improve and maintain your cybersecurity and protect your data. A suitable risk assessment would highlight any potential weaknesses.
What is the importance of cybersecurity?
Nowadays, the digital world, with all its possibilities, has become an offstage part of critical infrastructure. The worldwide network connects not only online shops and streaming services but also represents industries like healthcare, government, oil and gas, and manufacturing online. Data breaks in this type of business can affect the work and lives of thousands of people.
Moreover, we witnessed government digitalisation during the last decade. It made us more dependent on both high-level physical and cybersecurity. For example, the US government faced costs of over 13.7 billion US dollars as a result of hacker attacks.
What makes SMEs a hacker’s target?
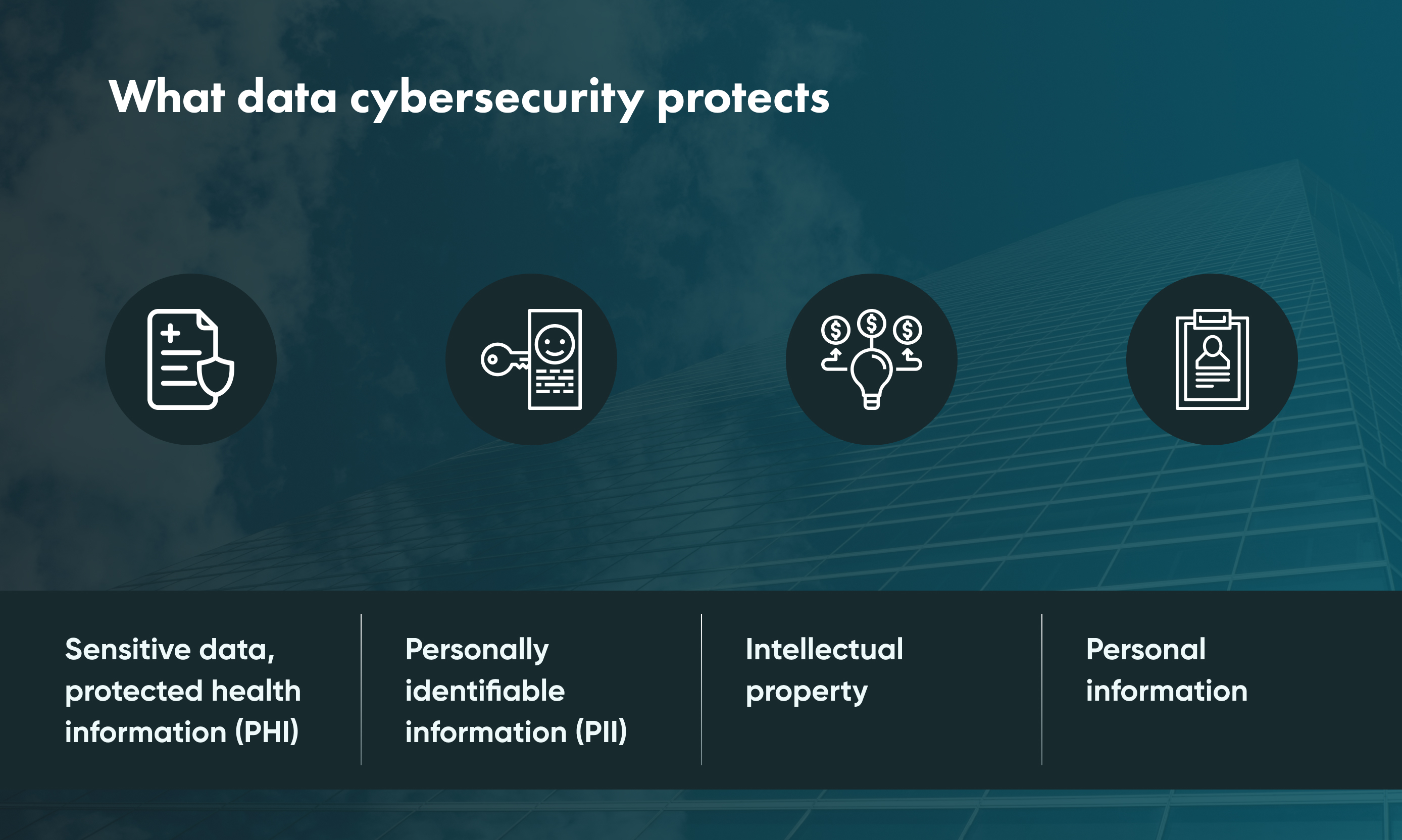
Valuable data
Depending on your business's niche or industry, you may have unique and high-value data. For example, clients' bases, research, bank account credentials, or anything else you collect during the working process might be a good and reasonable target for hackers.
The most common way for a cyberattacker to benefit from stolen data is by selling it on the dark web.
Hardware
Sometimes, hackers have nothing to do with stealing companies' sensitive data. Another popular reason to hack a company is to abuse its hardware. In that case, the computers become a part of hundreds of other broken devices and are used for DDoS attacks creating an unrealistically big flow of web traffic.
Link tree
Although big companies are mostly well protected from data hijacking, the smaller ones can still give access to them. This is because small and big businesses have a connection via links they both use to share data.
Money
It's the last but not the least reason to breach into SMEs' systems. Unfortunately, there are many ways to drain money from businesses to the last drop. Blackmailing, data selling– the list goes on.
Why cybersecurity presents unique risks for SMEs
Tight budget
It's no secret that smaller companies have a tighter budget for running their business. But, for some reason, cybersecurity might be considered a non-priority in spending.
At the same time, more prominent companies have the budget to hire cybersecurity experts and "ethical" hackers to find vulnerabilities. However, small and big businesses share similar IT security risks.
Complexity challenges
Many smaller teams lack the experience and know-how to do this effectively. Additionally, supply chains are growing longer and more complex. Hackers have adjusted their tactics and often attack the weak point in the chain (often an SME vendor) to help penetrate a larger enterprise with stronger security.
Expertise challenges
Small and medium-sized businesses can rarely afford a large in-house team of experts to run cybersecurity processes and create robust security systems. Unfortunately, this gap in security is commonly exploited for data thefts. They use small business systems as weak points in the chain to gain access to larger companies.
Types of threats for small businesses
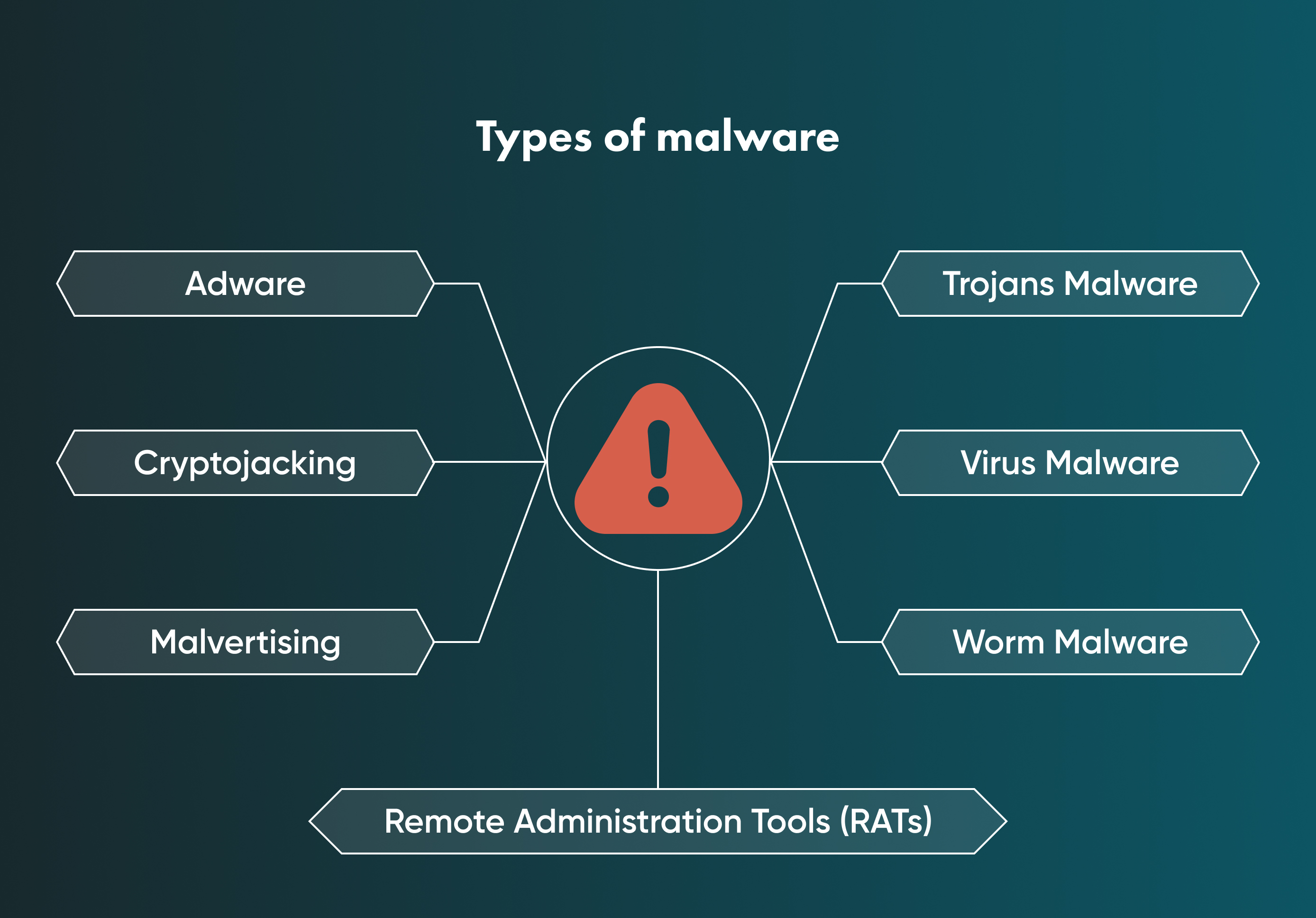
Malware attacks
Malware (or "malicious software") is the most popular way to attack computer systems. Malicious software is a file or code the targeted victim usually receives from the network via unprotected channels.
Although malware gives numerous options to damage the system, there are three main malevolent methods to find the victim: trojan horse malware, viruses, and worm malware.
The main risks that come from malware cyberattacks are giving hackers unsanctioned remote control and access to the infected device, losing unprotected sensitive data, receiving spam, and detecting the local network of the infected user.
Phishing
This threat type is possibly one of the most dangerous. Unlike malware, phishing is a social engineering attack, so catching this type of threat is mainly up to the users. Phishing programs make people click on it and share their sensitive data.
How? By masking as a familiar program or platform from which we often receive emails or texts. The data that can be stolen this way are passwords, credit card information, and so on.
Ransomware
This is a threat program that blocks users' access to their data or devices in order to get money. Ransomware is dangerous for both SME cybersecurity and that of individual users.
A good example of ransomware is the Cryptolocker. It is one of the first examples of how dangerous sophisticated ransomware can be. Let's see how it works. First, this program locks users' access to their own devices. Then, Cryptolocker uses a 2,048-bit RSA key pair and encrypted systems with all connected drives and synced cloud services.
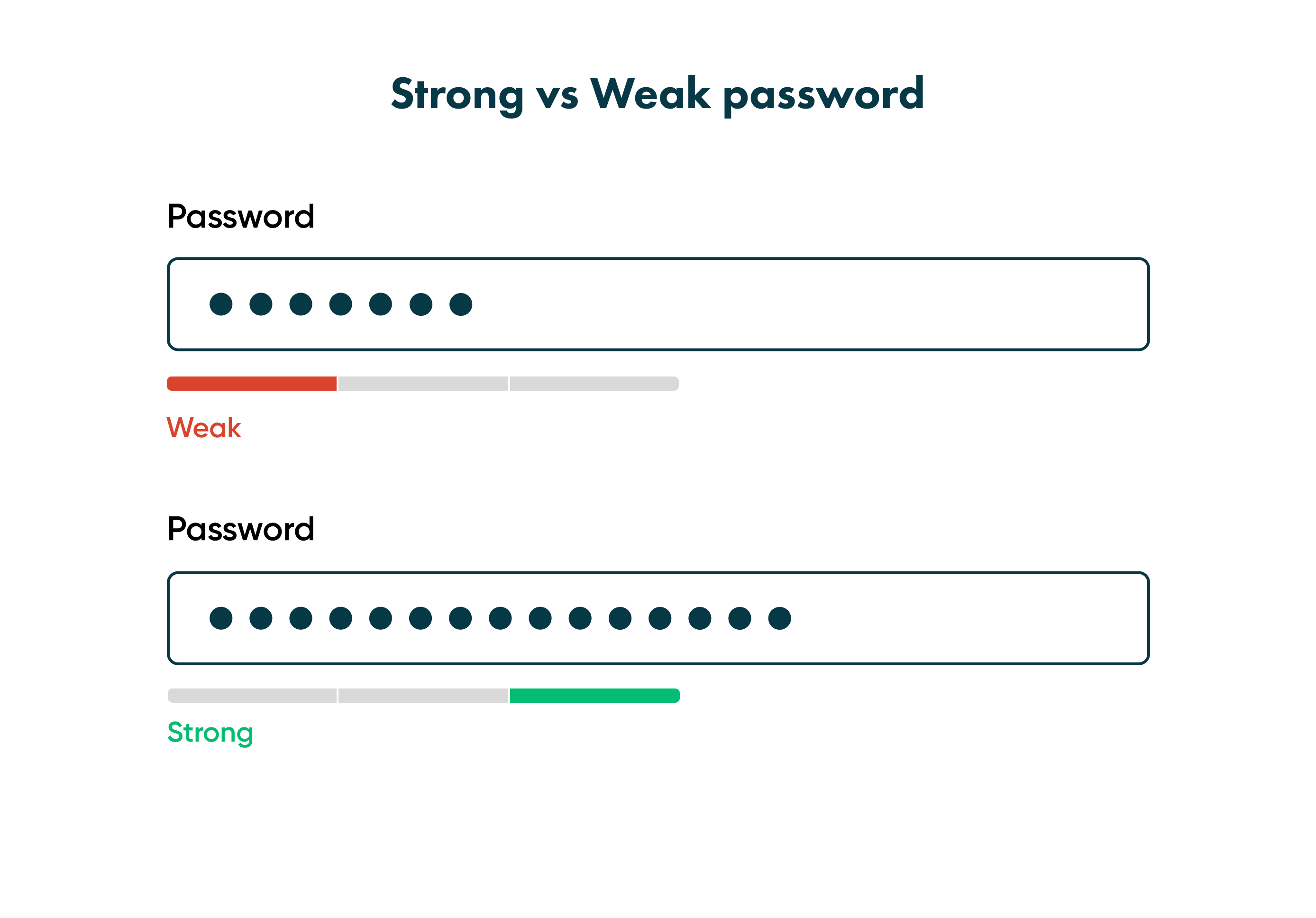
Weak password
Have you seen stickers with passwords on coworkers' PCs? If so, you witnessed a dangerous data breach possibility. Moreover, if this password is short or too easy to remember, the breaching options are even wider.
A weak password is short, standard, or even a system default symbols combination. Usually, it's birthdays, important dates, common words or numbers.
Insider threats
From the cybersecurity point of view, a zero-trust strategy is a good option to protect your data and devices. Sometimes people gain unauthorised access to sensitive data.
As long as anybody related to your company might be an insider threat, a cybersecurity system should be set for everybody equally.
Best practices to reduce cyberattack risks
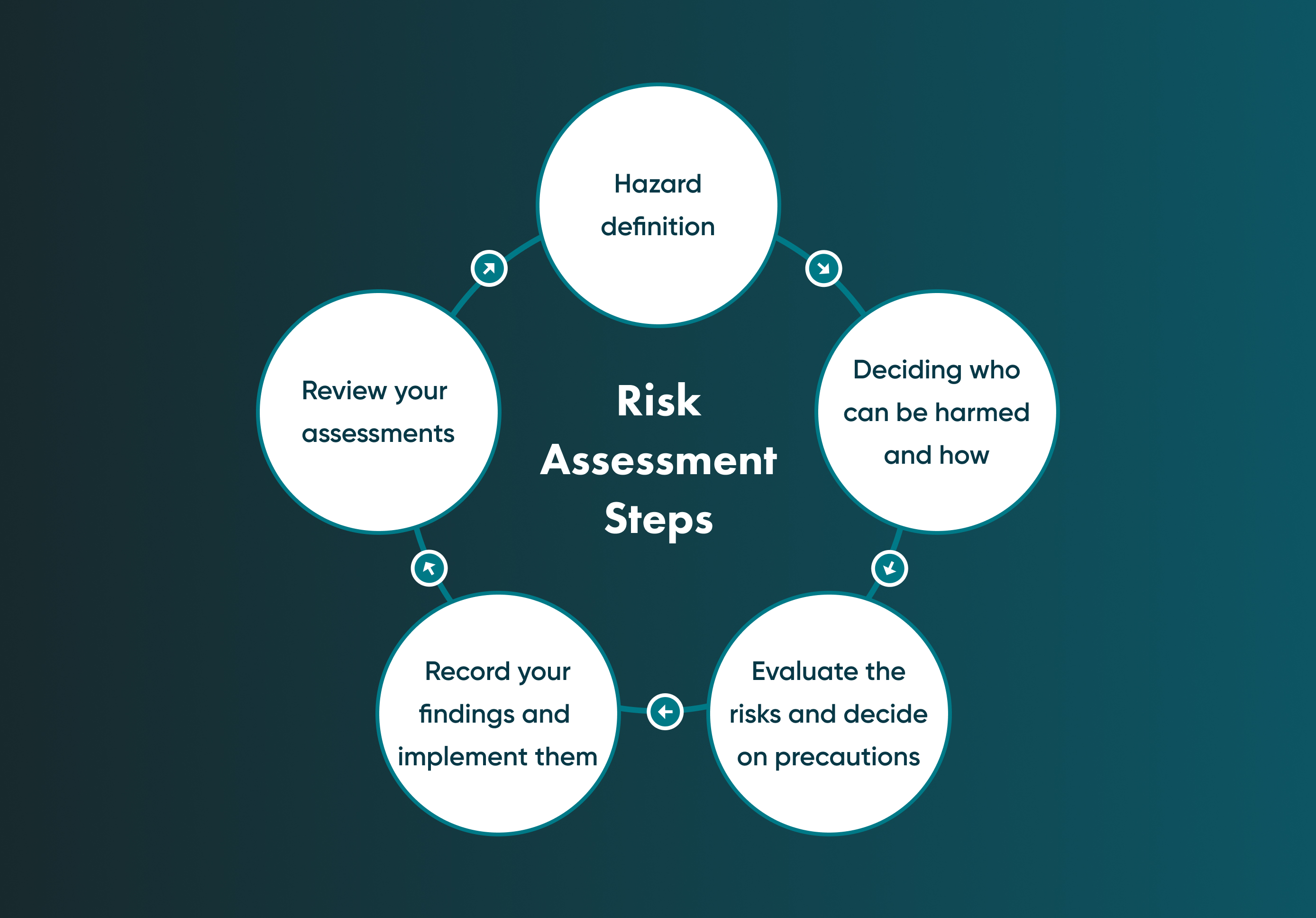
Security risk assessments process
A risk assessment helps business owners see their security system from the hackers' point of view. Thus, checking possible ways to break the company's security is an effective method of setting a holistic security plan with minimum defects.
Have a data security plan
The data security plan is one of the best practices for every company. It helps the team understand the steps they must take to prevent and recognise data breaches.
Having such a plan in place helps to avoid financial and reputational losses and benefits small and medium-sized businesses.
Train your employees to prevent insider threats
Employees and people with access to corporate data must understand what to look out for and how to keep sensitive data safe. A good decision is to take responsibility for their cybersecurity education and implement a security awareness training system.
Unfortunately, this is the aspect of inner security that business owners should increasingly keep an eye on. According to TechJury, insider incidents have risen by 44% from 2021-2022.
Implement a strong password policy
We already mentioned the danger that weak and unencrypted passwords bring to the organisation. And now it's time to talk more about how to avoid this mistake.
First, set a strict rules codex for employees. Secondly, always use password managers and create strong passwords according to cybersecurity requirements. In other cases, brute-force attacks or other password-breaking practices would easily crack your password.
Install firewalls
A firewall is a network security monitoring system that controls incoming and outgoing network traffic based on predetermined security rules. A firewall typically creates a barrier between a trusted and untrusted network, such as the internet.
Antivirus software is meant to protect your file system from unwanted programs, and a firewall helps keep intruders or external threats from accessing your system.

Contact GoWombat
This simple yet effective step would bring you to an expert team to help reduce your risks in information security.
Unlock Success with Premium Software Development
Contact us


Conclusion
Understanding your SME company's vulnerability is essential. For example, we all lock our office doors to stay safe and keep our important documents sealed in a safe. So why don't you cyber-secure your business? Basically, every unprotected way to access your data or devices is an open door for perpetrators.
In the long-term, increasing cybersecurity for small and medium enterprises saves money, avoids lawsuits, and keeps your and your partners’ and clients’ sensitive data safe.
Talk to our team at GoWombat to find out the best ways to manage your organisation’s cybersecurity.
How can we help you ?




