Cybersecurity Risk Management: What It Is and How to Apply It


When you do your business online, there are always associated risks. We have already written a lot about the importance of cybersecurity, but there’s still plenty left to explore. You should understand what cybersecurity risk management strategy means and why you need to know everything about it when you take your business online.
Have you looked into cybersecurity risk management? Security specialists must analyse your business and use their knowledge and experience to identify risks for business goals and assets. After this, they can build a plan to manage all cyber threats and ways to deal with them.
If you feel a bit out of the loop, don’t worry – here we spell everything out about cybersecurity risk management and the best practices to mitigate these risks.
What is cybersecurity risk management?
A cybersecurity risk is a potential threat to business assets, reputation, and income, or their comprehensive destruction. Cyber attackers strive to steal funds, information, or technologies.
Although these attacks are carried out in a digital environment, they present risks for the company on all levels. Cybersecurity risk should be aligned with the risk measurement, tracking, and mitigation system. Many companies take cybersecurity risks as a technical issue that should be solved. However, they are wrong.
Information cybersecurity risk management is a cyclical process consisting of risk identification, assessment, and mitigation of severe consequences in case of any emergencies. This process helps identify vulnerabilities in the security system and estimate the costs for their elimination.
The purpose of risk management is to protect the sensitive and valuable information of the company adequately. Therefore, a detailed analysis of all possible vulnerabilities is a necessary step.
This model of cybersecurity risk management is designed for the analysis process automation, logging the register of risks that includes not only a detailed description of vulnerabilities but also the likelihood of a threat being realised, as well as assets at risk.
Create your software with proper cybersecurity in mind — Let Go Wombat be your guide. Contact us!
What does cybersecurity risk management do?
Let’s check the list of the primary activities the cybersecurity risk management solution allows your company to do.
- Identify the risk map of the company.
- Draw up the list of current threats to information security.
- Draw up the list of vulnerabilities that can be used to carry out the threats.
- Draw up the list of protection measures.
- Identify the assessment area and collect comprehensive information about current business processes.
- Draw up threat models for each asset of the company.
- Conduct a comprehensive automated security risk assessment with the involvement of security experts.
- Develop a detailed plan of risk processing, and monitor its implementation and results of applying protective measures.
- Let employees conduct a rapid assessment of their business processes.
The advantages of risk management in cybersecurity
Implementing a cybersecurity risk management policy bears multiple benefits for the business. We list the six primary reasons you need to manage risks in cybersecurity.
Business reputation maintenance
If you don’t follow the appropriate risk management process in cybersecurity, a major data breach can become the reason for a fatal failure and loss of your customers. Your reputation depends on customer loyalty and their trust in your business. Thus, a well-elaborated risk management plan will help you be prepared for any malicious attacks.
Avoid financial loss
Financial losses are the most painful for any company. According to IBM, the global average total cost of a data breach is $4.35 million. So, it is essential to protect your business to prevent financial losses and stay afloat. In addition, remember that a data breach is connected with data privacy laws compliance, so your business will also need to pay fines for the violation.
IT department support enhancement
IT specialists in your organisation will be prepared for cyber attacks and associated situations if they have a risk management plan. Employees will be trained to take appropriate actions to protect the internal environment and the company’s resources from theft.
Downtimes reduction
If any breach occurs, it means that the company needs to eliminate the consequences and quickly deal with the situation, solving arising issues. Such activities lead to downtimes, the business doesn’t generate profit at this time, and employees focus on other tasks. Thus, risk management will be a helpful approach to minimise costs and reduce possible downtimes.
Higher productivity
Don’t forget that a data breach may lead to the loss and disclosure of all information, not only customers’ and partners’ sensitive data. Your employees’ data can also be under attack, and it will negatively impact their productivity if this data is stolen. Employees will work more efficiently when they know the company is aware of risk management and prepared for it.
Competitiveness
Forewarned is forearmed. When your company is ready to manage cybersecurity risks and has the required knowledge, you will probably stay ahead of competitors who ignore risk management strategy and hope that data breaches won’t be their concern. You will prove to your customers that cybersecurity is something you are always taking seriously.
The cybersecurity risk management process: step-by-step
What should you do to manage risks? You need to take several steps to initiate the cyber risk management strategy. The type of steps may vary depending on your business and its particularities, but we describe the main steps that are regularly taken.

1) Identify the most common risks
We have already listed in detail the most common cyber risks in our article about cybersecurity. You need to read it carefully to understand more. So your first step is to identify the vulnerabilities and risks that may use these vulnerabilities to damage your business. As it is said — look at you enemy in the face.
2) Assess the severity of risks
Once you identify potential risks for cybersecurity, you should analyse how each threat may be harmful to your business processes and what potential negative impacts it may lead to. After this, you should go to the next step.
3) Risk prioritisation
The severity of risks will help you prioritise them and know what risks are more dangerous, in order to pay careful attention to them first. The correct prioritisation is the right way to build a cyber risk management process and know what threats can become a real headache for your business.
4) Response to each risk and their mitigation
Here, you should understand how to respond to and mitigate each risk. There is a response plan that you should have, and you will find this plan below because it is rather large. You can modify the risk’s likelihood, retain it if it falls within a risk acceptance criteria, or terminate it.
5) Monitoring
The cybersecurity risk management process is a long-term process. Your IT team will need to monitor all potential risks to stay updated and keep track of regulatory changes and internal IT technologies use.
The cybersecurity risk management process is a long-term process. Your IT team will need to monitor all potential risks to stay updated and keep track of regulatory changes and internal IT technologies use.
Important frameworks to manage risks in cybersecurity
Another crucial step to consider is using cybersecurity compliance frameworks that include requirements and relevant practices to manage cyber risks efficiently. The four most popular frameworks are mentioned below:

PCI-DSS
Payment Card Industry Data Security Standards, or PCI-DSS, is an information security standard that should be complied with by all organisations which handle payment card transactions. PCI-DSS is the list of requirements and regulations regarding the data privacy of cardholders. You must use PCI-DSS to protect your customers' financial data if your business involves such financial operations.
ISO/IEC 27001
One of the most well-known international standards that sets the requirements for the information security management system. The ISO/IEC 27001 certificate is the document that proves your system complies with security standards, and partners/customers can be confident that your company protects all data from unauthorised access.
NIST cybersecurity framework
Another cybersecurity risk management framework represents a framework based on existing standards and practices for private companies in the US, which helps them manage cyber risks and mitigate them.
CIS critical security controls
CIS stands for the Center for Internet Security, which provides an essential set of actions to form a reliable and well-proven security system and protect your network from cyber attacks, minimise data breaches, corporate espionage, etc.
Do you want to secure your software but need to know how? Go Wombat will provide you with a detailed consultation — contact us!
Ways to enhance your cybersecurity risk management program
Apart from the above-mentioned steps, there are a few tips to improve your cybersecurity risk management solution, and we are glad to share them.
Advanced encryption
Encryption is not a new approach in the cybersecurity world, but it remains current and essential for today. Data encryption means that a piece of information is converted into code, and you cannot decrypt it without a key. There are three primary encryption types — AES, 3DES, and RSA. You must use these encryption methods to protect the sensitive data your business works with.
Data redaction
Redaction is the form of limiting access to specific information in cybersecurity. Simply put, companies can share information, concealing sensitive data, so third parties can see only those data that cannot be compromised and used in fraudulent schemes.
Limited role-based access
Finally, access to sensitive information should also be limited within the company. Thus, only specific employees can access this information if their job is closely related to processing such data. It will also increase the security level and simplify the risk management process.
The cybersecurity risk management plan: the response to risks
The response plan is the plan that will help you recover from cyber attacks since attacks will happen regardless of how strong your security system is. The response plan includes a few guidelines on what steps you should take in case of any cyber attacks.
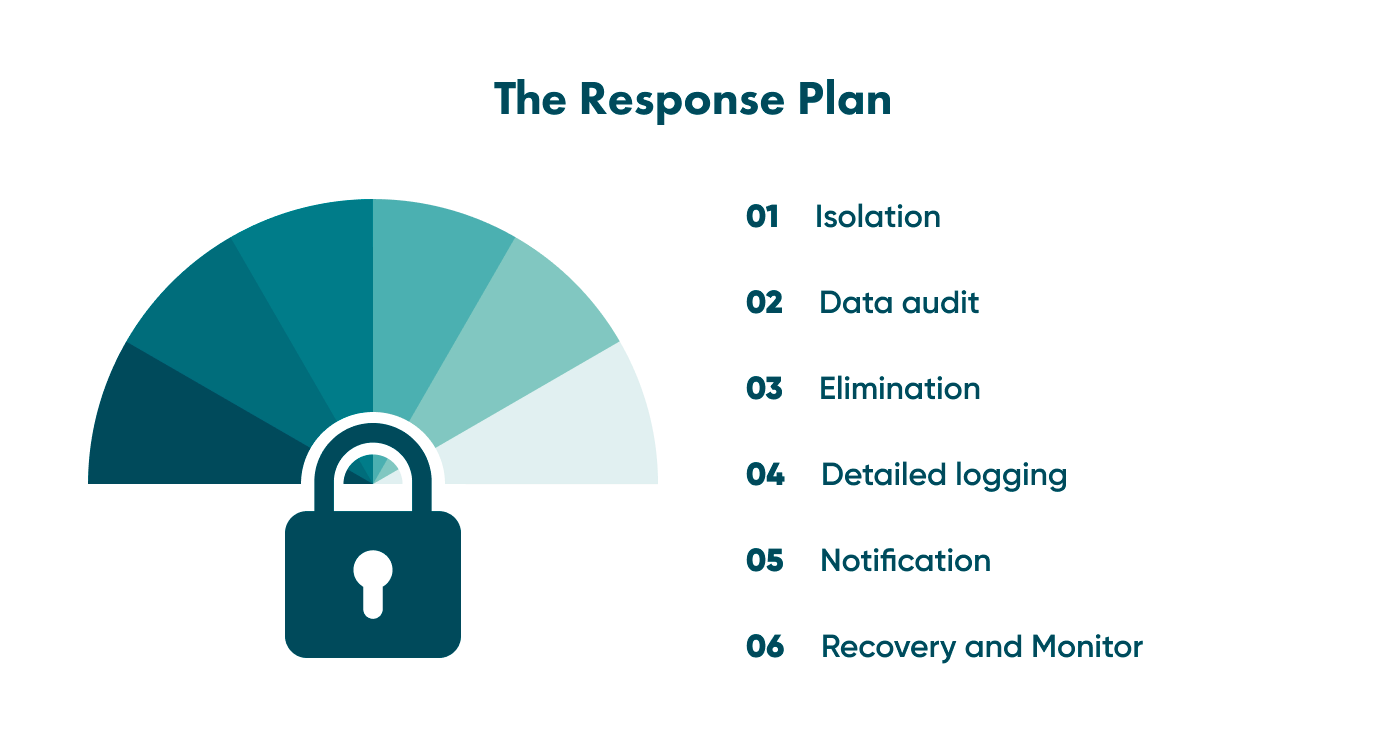
Isolation. You need to isolate the systems and software that were attacked to avoid spreading the threat.
Data audit. After the attack occurs, you need to check all the sensitive data to identify how much of it was (or wasn’t) corrupted to assess possible risks.
Elimination. You should eliminate all infected files and replace software (if necessary) or even hardware.
Detailed logging. You must keep a log of all attack details and your response. It will help you deal with attacks more effectively and avoid mistakes in future.
Notification. You must notify your partners or customers about a data breach within the set period, especially when your business complies with the GDPR. For example, under the GDPR, you must notify customers about a data breach within 72 hours. Thus, you won’t be fined and can start applying recovery measures.
Recovery and monitoring. Now you need to do your best to recover the lost information (don’t forget about back-ups) and all other consequences of cyber attacks. Also, keep monitoring the situation to prevent a new episode.
Taking action
It should be clear now that having a risk management plan is essential for protecting your organisation's cybersecurity. You should be prepared for risks, know how to mitigate them, and prevent your business from severe losses.
If you are not skilled in this field, it will be very challenging to start applying preventive measures and using appropriate cybersecurity risk management software. That is where Go Wombat comes to the rescue. Our company has a Chief Information Security Officer who ensures that your software and digital assets are appropriately protected.
Go Wombat creates software of any complexity, and its security is our primary concern. We at Go Wombat always strive our best to make your business secure.
Let’s make your business safe together — contact Go Wombat!
Unlock Success with Premium Software Development
Contact us


FAQ
What is risk management in cyber security?
Risk management in cybersecurity is the process of identifying and analysing the most common security risks. This process helps you stay alert and protect your digital environment from potential cyber threats.
How do you conduct risk management in cyber security?
First, we need to determine the information value, identify and prioritise assets, identify potential cyber risks (threats), understand the vulnerabilities of your business, assess risks, and develop scenarios for different situations (the response plan). That’s plenty to start with. However, the risk management process may vary depending on each individual case.
Why is cybersecurity risk management important?
The answer is quite simple — without a proper cybersecurity risk management solution, your business won’t be prepared for potential cyber threats, and you won’t have the plan to deal with risks and mitigate them. It will lead to severe financial and reputational losses.
What are the 3 steps of security risk assessment?
These are the primary three steps:
- Identify the most common risks
- Identify the most common risks and your vulnerabilities
- Prioritise these risks to determine which are the most dangerous
How can we help you ?






