How To Secure A SCADA System


Protect your System from From Malicious Attacks
An enterprise utilises many specific systems and tools to control all its activities, especially for managing the provision of essential services like water, electricity, and gas to people. Industrial enterprises must use different systems to ensure that everything functions appropriately without interruptions.
Multiple industries choose to incorporate The SCADA system (Supervisory Control And Data Acquisition) for such purposes. It collects all vital information about the current processes of the factory or any other enterprise. However, if there are some security breaches, all data received may be at risk. It could affect not only the enterprise itself but customers as well. Therefore, securing the SCADA system from all external threats is crucial.
Within this article, we will explore details about SCADA such as the structure and benefits. We will also look into any possible threats. Finally, we will outline the steps required to secure a SCADA system.
What Is SCADA?
The SCADA system is a system that collects information about the current activities of an enterprise and allows specialists to control collected data. SCADA can provide specific information from various facility points in a real-time mode. It enables a smooth and optimised management of an enterprise without emergencies, failures, or downtime.
The control and monitoring of multiple remote objects is the primary purpose of SCADA systems. The primary users of SCADA systems are distribution substations, oil pipelines, gas pipelines, and water or gas supply systems. Predominantly, we incorporate SCADA in any industry where real-time automated control of technical processes is required.
A supervisor interacts with software installed on a PC, and input/output drivers and related servers connect with controlled objects.
At Go Wombat, one of our fields of activity is the development of SCADA systems for various organisations (oil & gas industry, and manufacturing).
The General Structure Of A SCADA System
Three components of SCADA
Remote Terminal Unit (RTU).
We use it for processing information in a real-time mode. RTUs can be sensors that collect data at a given interval. However, up-to-date solutions represent multiprocessing fault-tolerant computation units, and they process information continuously in a real-time mode.
Master Terminal Unit (MTU).
A primary terminal unit where specialists process all information collected from all RTUs. The main purpose of MTUs is to create a human-machine interface that contributes to effective interaction between supervisors and an automated process control system. MTU is the unit where all security practices are to be applied.
Communication System (CS).
The third unit implies connecting components between remote objects and MTU.
The SCADA system is similar to the Internet of Things, but these are two different technologies. We will cover this information in detail in the following article.
Does your company need a SCADA system? Then contact Go Wombat to build it from scratch.
Why SCADA Is Important
The SCADA system has many advantages, many of which are listed below.
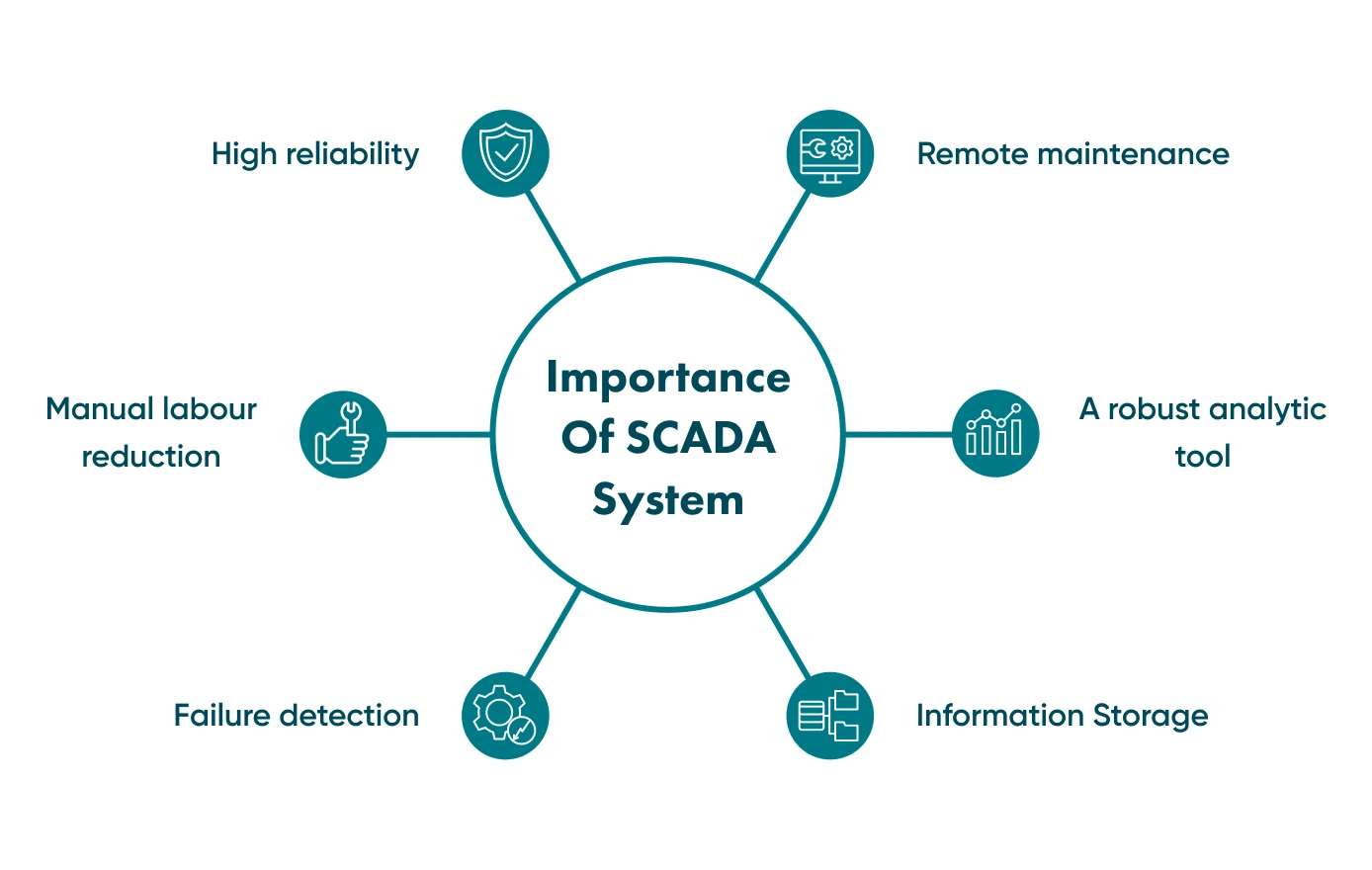
High reliability
The SCADA control process is fully automated 24/7, so humans can rely on the SCADA system that continuously collects all data.
The reduction of manual labour
Closely related to the previous advantage, specialists do not need to collect information manually, allowing them to increase their performance.
Failure detection
The SCADA system can notify the supervisor about any failures in the system so that the specialist can fix them immediately.
Remote maintenance
Many failures can be fixed remotely, and there is no need to send specialists to distant objects. Furthermore, the system can even fix some failures in an automated mode.
A robust analytic tool
SCADA provides tools for analysis and system diagnostics. These tools help increase maintenance efficiency and recommend sectors where modernisation is required.
Information storage
All collected information is stored on servers, and it is possible to extract the data, analyse it and use it to increase the performance of the enterprise.
Threats SCADA Systems May Face
Systems that contain sensitive data are always at risk since cyber attackers are looking for fraudulent ways to gain access. There are several threats control systems may face, in particular:
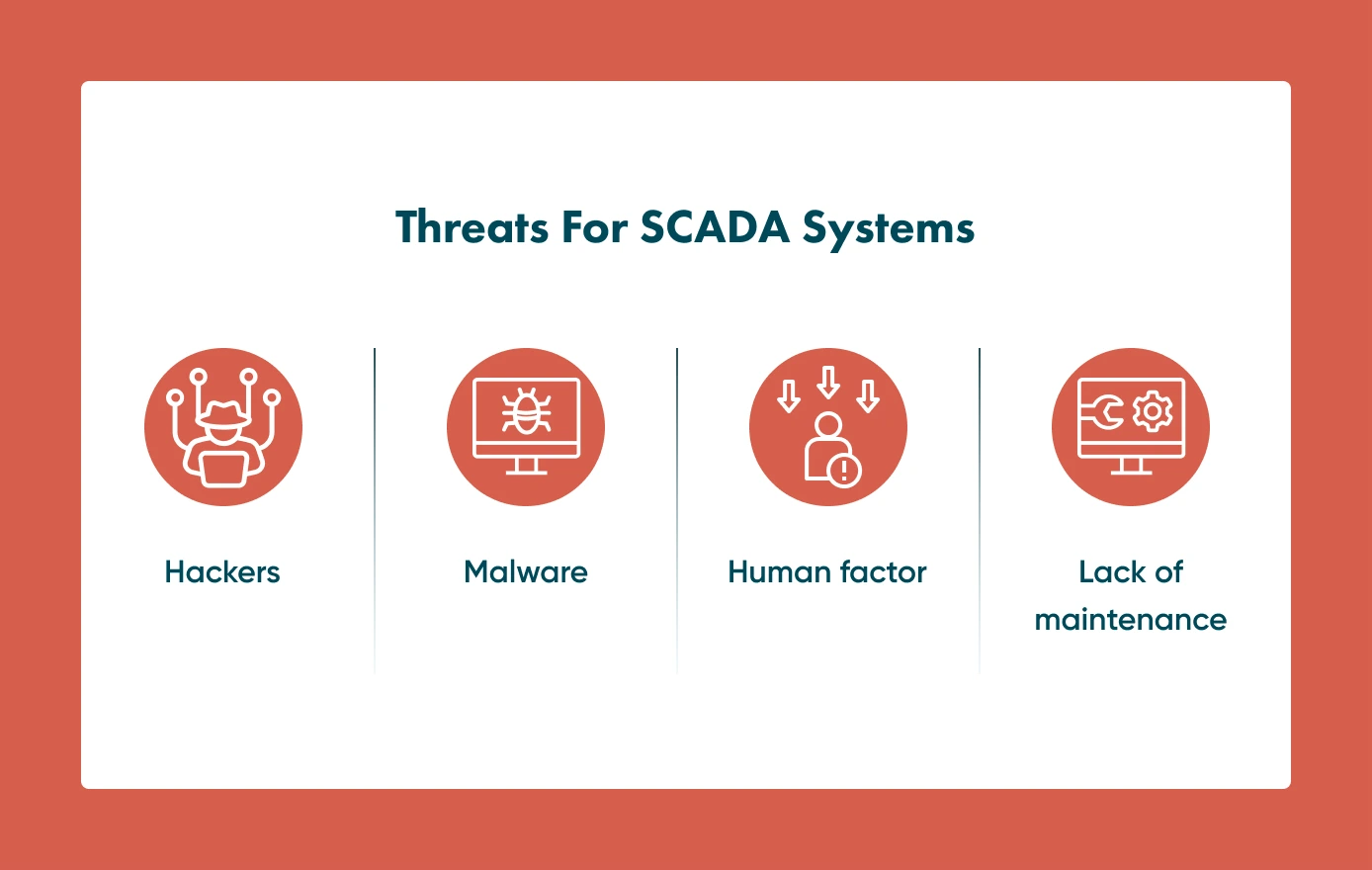
Hackers
The first and the most dangerous threat is cyber attackers looking for security breaches. They can steal the information and demand a ransom or even use it for their own criminal purposes.
Malware
Malware is malicious software that makes specific changes in your software and may damage its performance. Although malware is not commonly used to damage SCADA systems, it remains dangerous for a digital business environment. Employees should be aware of it when they want to click links in unusual emails or visit unknown websites.
Human factor
People make mistakes. Even unintentional errors can lead to security breaches. Linked with this is the lack of training which is a real risk for the SCADA system. Therefore, it is required to organise regular training for all employees working with SCADA systems.
Lack of maintenance
The following important issue is permanent updates of software and hardware. At Go Wombat, we can keep maintaining the SCADA software we created, so we ensure it remains up-to-date and secure.
If you feel you have security issues. Go Wombat can help fix them — contact us!
Steps To Secure SCADA Systems
These steps are essential, but some of them require technical skills. So we recommend cooperating with a software development company.
Here, we share our experience and provide valuable tips on how Go Wombat can help protect a SCADA system from any external threat.
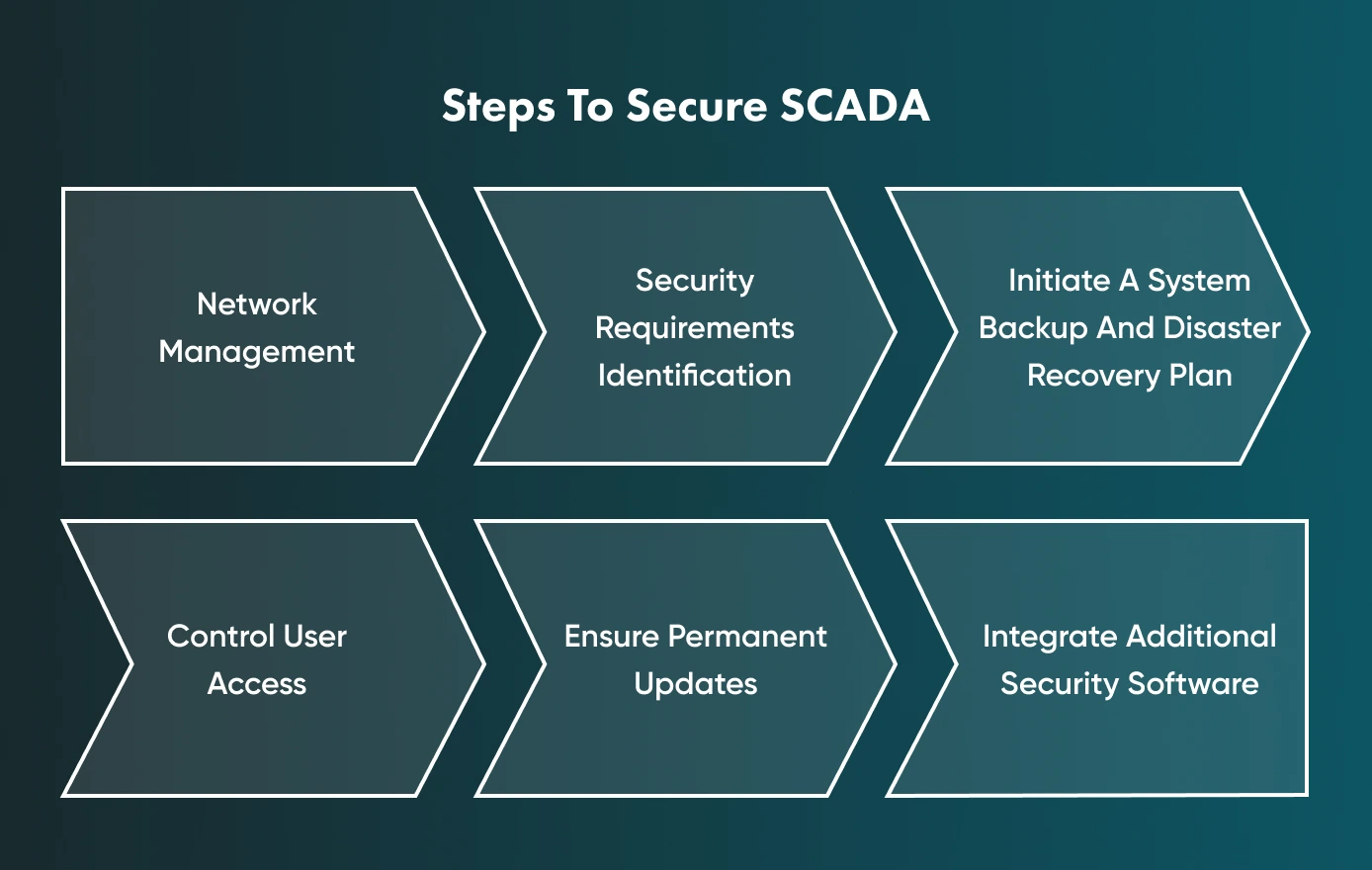
Network Management
First, it is crucial to understand system assets. For example, if you need Go Wombat to secure an existing SCADA system that we have not created, we would need to analyse your system and assess all potential vulnerabilities and risks.
As a result, we would apply relevant security techniques. We need to map out all SCADA network assets, connection points, and user accounts before identifying how we can secure your system appropriately. Without identifying your system’s weak points, it is impossible to protect it as required.
Security Requirements Identification
When your company uses a SCADA system, it must have a structured security program with requirements for technical staff who work with SCADA systems. Its purpose is to provide a standards-based approach to cyber security methods so that employees will know the required protection techniques, they will understand their responsibilities, and what they should do in case of emergency.
Go Wombat can also help draw up cyber security requirements for your organisation to minimise potential threats and provide required security standards that all employees should follow.
System Backup And Disaster Recovery Plan (DRP)
A DRP implies the instructions for assigned employees on how to recover the system once a sudden disaster occurs. Furthermore, we strongly recommend establishing a system backup in the event of critical information loss. It would be possible to restore information, and any emergency would not damage your system. As important as it is to initiate a system backup and DRP, it is also advisable to train your staff on how to follow all the instructions properly.
Control User Access
The next step is to manage user access when many users work with one SCADA system, and each of them has access to it. Go Wombat can create user access levels according to the hierarchy of your staff. It means that each user should have access only to their level of responsibility. When there is no strict user access level, the system becomes more vulnerable, negatively affecting the overall cyber security situation.
Important note! Passwords must be changed regularly. There is no strict rule, but it is recommended to change them once per two or three months.
Ensure Permanent Updates
This is the recommendation we have mentioned above in the Threats section. Software and hardware become outdated, and it is important to update them regularly. Go Wombat recommends creating an internal policy that stipulates permanent updates within the indicated period. It would be a win-win: the SCADA system works better, and the security level increases.
Go Wombat always works on improving software, so we create up-to-date security solutions for all projects we build and maintain. Our certified Chief Cybersecurity Officer (CSO) is in charge of this part of the work.
Additional Security Software
The last but not least piece of advice from Go Wombat is to add appropriate software options that will enhance the security of your SCADA system. For example, we assert that your network should have firewalls (it is a basic yet must-have option to block unwanted traffic and threats), unidirectional security gateways (USG) which provide an extra security layer for your network (a combination of hardware and software that allows data to travel in only one direction), intrusion detection systems that notify immediately about any unauthorised access into the network.
Finally, regular security audits are essential. Our CSO will audit your network and conduct penetration tests to ensure the stability and high performance of the SCADA system.
Unlock Success with Premium Software Development
Contact us


Drawing The Line
The protection of the SCADA system is a time-consuming yet fundamental process. The primary goal of Go Wombat is to smooth this process and relieve you of this headache. We think our guide will explain to you what steps you should take to understand how it works, but eventually, you may entrust the project to our company.
Apart from our CSO’s security certifications, he has also become a Certified Data Protection Officer, which means that he is certified in how to adhere to the GDPR security requirements and make your software compatible with it (an essential aspect for any product for the European market).
Contact us to make your SCADA system secure and reliable — Go Wombat is at your service!
How can we help you ?






