Mobile App Security: Protecting User Data and Preventing Cyber Breaches


Developing a mobile app for your company is an exciting task, whether it’s for your customers or for your internal team. But, as with any other piece of software, you need to abide by the highest mobile app security standards if you want to protect your platform from cyberattacks and set it up for success.
With the above in mind, mobile application security is a huge field that encompasses user authentication and authorisation as well as a collection of other variables.
Fortunately, at Go Wombat we specialise in building powerful mobile applications that are not only tailored to your needs, but also adhere to the highest standards in terms of security.
Let’s go over the different security elements you should consider when building your application. We’ll also share 6 mobile application security tips and best practices you should follow when building an app for your business.
Understanding Mobile App Security
Mobile app security testing is among the key steps you need to take to ensure a safe application.
But, what is mobile app security in the first place? And, when do you have to worry about it?
For starters, mobile application security refers to the steps you take and the systems you put in place to protect your apps from the different cybersecurity threats out there. This encompasses:
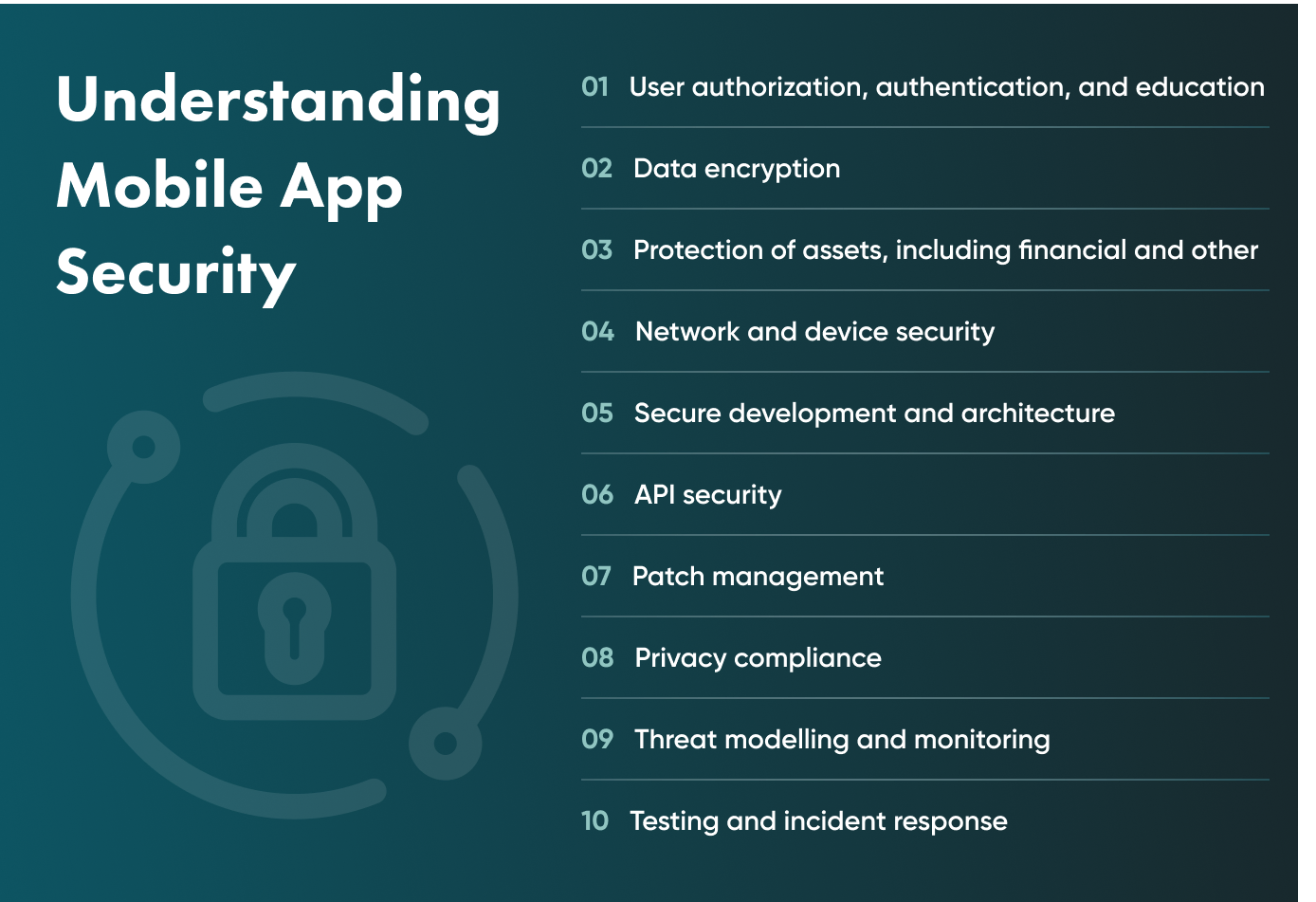
Let’s take a closer look at each variable and how it impacts security.
User authorisation, authentication, and education
While security testing of mobile apps is essential, it’s also important to start protecting your app at the most basic level: the end user.
Depending on your app, users should be able to log in, prove their identity, and use every feature of your app without peril. So, you have to ensure that your user authorisation and authentication systems are airtight.
In addition, users need to be aware that they are in a unique position because they can accidentally contribute to a breach by providing access to hackers and similar criminals.
Because of this, it’s always a good idea to create educational material and advise users of standard best practices, like avoiding password sharing.
Data encryption
Data encryption is the act of encoding the incoming and outgoing data of your mobile app. If not, it’s possible for criminals to intercept these messages and extract either sensitive information or data that can later be used in another attack.
If your app will collect, store, and/or transmit sensitive details, it’s strongly advised to encrypt your software to help improve your mobile apps’ security.
Protection of assets, including financial and other
There are many variables that impact the security. Mobile apps can save payment information, store cryptocurrency assets, and hold other valuable assets.
If you’re worried about security for mobile apps you want to develop, it’s important to determine all of the areas that need to be protected.
To create a truly safe application that protects your assets, your security plan will have to address every aspect found on this list as well as new threats later on.
Network and device security
When it comes to mobile application protection, you also have to consider both device and network security. And, while these require separate processes, you should carefully consider how a single compromised device may impact your entire network security.
At this point, it’s necessary to consider the OS types and versions you will serve. This will help guide you during the app security testing stage as you will know exactly which devices your app will be installed on.
Secure architecture and development
The architecture and development process are closely linked for a variety of reasons. One of them is that both need to be secure for your application to be protected against criminal threats.
Now, note that the selection of architecture and development processes occur at different stages. As such, you need to keep user safety in mind from the moment you start creating the architecture, continue through the development process, and up until you finish the security testing for your mobile apps.
API security
APIs can help integrate your app with other platforms. But, every additional interface that’s added to your application represents a potential security risk.
It’s essential to ensure your app is only accessible to other applications that maintain high security standards.
The good news is that securing your API involves similar techniques to protecting your network, such as implementing data encryption and monitoring for unusual activity. Just remember to add this to your mobile application security checklist!
Privacy compliance
It doesn’t matter if you’re focusing on iOS or Android app security, your application needs to abide by any and all relevant regulations.
Depending on your industry, application type, and location, this may mean adhering to GDPR, HIPAA, and other local regulations.
Not sure what you need to focus on? Contact Go Wombat and our compliance consultants can verify that your application adheres to all regulations before its launch.
Threat modelling and monitoring
Threat modelling and monitoring refers to two distinct steps: the simulation of different attacks on your secure mobile apps to test their response and the monitoring of live threats in order to respond accordingly.
Like many others on this list, these two are linked because your modelling influences the efficacy of your monitoring system. It’s relatively straightforward – if you focus on creating different models, it increases your chances of identifying attacks quickly and accurately.
Vulnerability and incident response testing
As we’ve mentioned several times by now, mobile application vulnerability testing is a must in any development project. In short, this process allows you to uncover potential weaknesses and address them before your app goes live.
Now, there’s another necessary step that needs to be evaluated at the same time – incidence response. It’s important to note that vulnerability testing and incidence response testing are two different processes, but you can perform them one after the other to ensure your entire system reacts as intended.
Payment security
Payment security doesn’t apply to every single application.
But, if your app lets users make payments, store payment details, or otherwise perform financial transactions, then you need to decide how you will protect these activities.
Here are some of the steps you’ll want to follow to boost your payment security.
- Use a secure payment gateway
- Tokenise payment data
- Use the highest possible authentication level
- Encrypt your payment portal
- Minimise the collection of data as much as possible
- Perform regular security audits and implement upgrades accordingly
6 Secure development tips and best practices
Now that we’ve covered the basics, here are 6 tips and best practices that can help you protect your mobile application.
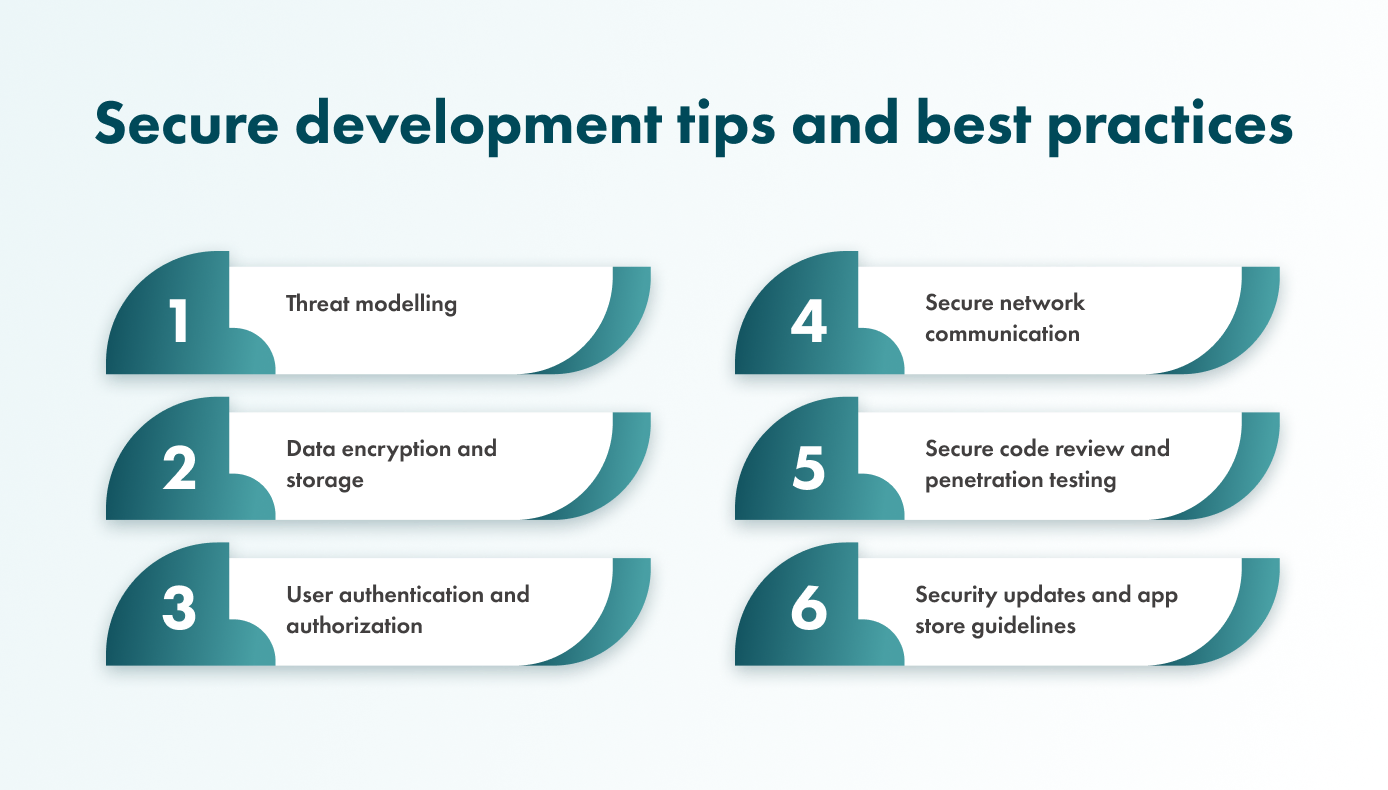
1. Threat modelling
We’ve already provided a stealthy threat modelling best practice in this article, so here’s the second tip around this topic: make sure to review, assess, and improve (where necessary) your app’s security controls.
In simple terms, you should evaluate individual threats and consider the mechanism they use to gain control of your app. Then, follow each one of these paths yourself. Make sure to make a note and implement improvements whenever you find a control path that has a weak or missing security threshold.
Keep in mind that threat models should be used, so try out each attack method at least once while security testing mobile apps.
2. Data encryption and storage
As you can imagine, the idea here is to implement secure data encryption and storage.
The type of encryption you choose is just as important as mobile app security management. So, make sure to discuss this with your team or get assistance from our security consultants before deciding on the best option.
The same goes with storage – from in-house to cloud and hybrid, each one has a unique setup and thus requires a distinct type of security strategy. Your company likely requires a fully tailored approach, so get in touch with us if you want to have our professionals set you up.
3. User authentication and authorization
If you want to build secure mobile applications then you have to provide world-class authentication and authorisation mechanisms.
Here the best practice is simple – make multi-factor authentication an option and encourage all of the app users to use it. This will help eliminate a large portion of password-related breaches – up to 99.9% according to Microsoft.
4. Secure network communication
When it comes to securing your network communications, encryption is the best place to start.
Here, the preferred method is using HTTPS (HTTP Secure) to encrypt data that’s being transmitted between your app and its servers using TLS/SSL protocols, the highest standards used on the web today.
In addition to this, you should:
- Use certificate pinning to limit communication with your designated servers.
- Create a system to sanitise and validate user input.
- Configure security settings like hostname and certificate validation.
- Segment your network to prevent attacks from spilling into your entire operation.
- Scan your network and implement modelling/testing to maintain its integrity.
5. Secure code review and penetration testing
As part of your security testing for mobile applications, take the time to perform a secure code review. Simply put, this consists of periodic reviews where you analyse the source code of your app, with the goal of identifying vulnerabilities, weaknesses, and other areas of improvement.
When reviewing your code, make sure to:
- Establish guidelines before starting to ensure consistency.
- Use static code analysis tools when available.
- Have your code reviewed by peers.
- Spend more time on high-risk, high-reward areas.
- Examine third-party libraries to make sure their code is clean.
By consistently conducting secure code reviews, you can identify and address security vulnerabilities early, create a more resilient mobile app, and contribute to a strong security posture for your application and its users.
6. Security updates and app store guidelines
As with all of the analyses you perform, you should aim to learn from your security testing for mobile application security.
Rather than simply noting the weaknesses, work on creating a new version of your app that’s more secure. You can pair this with the deployment of new features to engage your users and build more excitement about the updates.
Additionally, take the time to ensure you’re adhering to whichever app store guidelines apply to you. If it will be available to the public, your app should also be verified by all relevant stores in order to give your users more peace of mind.
Unlock Success with Premium Software Development
Contact us


Conclusion
Creating a mobile app from scratch is a unique process because every application is different. But, one thing they all have in common is that they need to possess great security features in order to provide users with the best possible experience.
We hope that the explanation above helps you understand some of the security aspects of building a mobile app for your company. Not only this, our tips are designed to guide you through your project and ensure that your developers have a basic guide to follow.
Need help securing your app? Our team will be glad to help. Just book a consultation and we’ll get back to you as soon as possible.
How can we help you ?






