Top Cybersecurity Threats in 2023: How to Protect Your Software


The global cost of cybercrime will surpass the $10.5 trillion annual mark by 2025.
This is, without a doubt, an astounding figure. Unfortunately, it also means that the risk of suffering damages due to a cyberattack are extremely high.
What are cybersecurity threats the most dangerous? How to prevent your network from attacks? What types of threats exist?
In our detailed article, you will find answers to all these questions and more.
Let’s dive right in.
What is a cybersecurity threat?
Cybersecurity threats are any form of activity that compromises your network’s integrity. In many cases, these threats come from digital criminals aiming to take advantage of an individual in your team or your entire organisation.
The goal of cybercriminals is to damage computer networks, steal data, extract valuable assets, extort their victims in exchange for money, and conduct other forms of crimes online.
Common categories of current cybersecurity threats include malicious software, social engineering, man-in-the-middle or MitM attacks, DDoS attacks, and SQL injections. We will cover each one later in this article.
Digital threats can come from different sources: individual hackers, criminal groups, and even malicious team members who want to commit illegal acts.
Therefore, it’s essential for all businesses to have a comprehensive cybersecurity system to mitigate all potential scenarios.
Generally speaking, cybersecurity threats can be divided into two categories: natural and artificial.
-
Natural threats are disasters like floods, hurricanes, fires, and similar events outside of human control.
-
Artificial threats come directly from humans, and they can be intentional or unintentional.
- Unintentional threats arise due to carelessness, inattention, and from similar errors. For example, a person installs software that isn’t required for the job, but can damage the system functionality and lead to data theft.
- Intentional threats mean cyberattacks by criminals, and each cyberattack leads to financial and intellectual property loss.
Why is cybersecurity or protection from cyberattacks important?
Cybersecurity measures are critical in various industries and scenarios.
For example, they help protect confidential details like medical data, intellectual property, and government information from theft and its subsequent use.
Yet today it feels like the chances of falling victim to cybercriminals is at an all-time high.
This is the reason why everything that is stored online should be protected by multiple security layers.
Both everyday users and large companies alike employ various cloud services for personal data storage.
Even giant cloud services like AWS and Google Drive are not immune to cyberthreats like:
- New forms of attacks that feature innovative technologies
- Lack of cybersecurity knowledge at the employee level
- Outdated online security best practices
It is clear that companies and organisations are the main targets of attackers. But these criminals can exploit a wide range of areas, including your cloud services.
Ask for assistance from our reliable specialists in cybersecurity at Go Wombat.
Sources and types of cyberthreats
Before we proceed to the most critical security threats, it’s important to understand where threats come from and vulnerabilities that may be exploited.
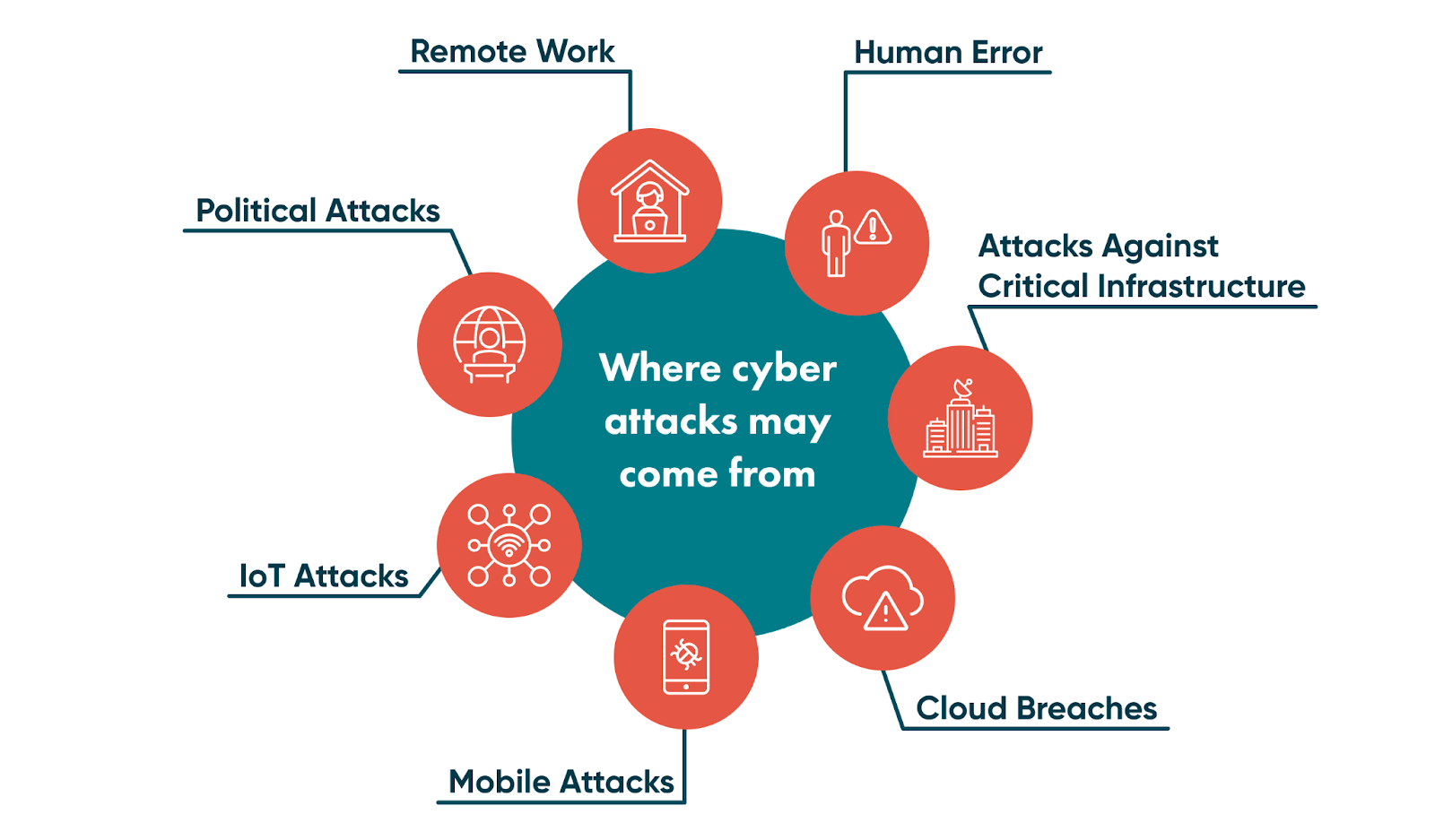
Cloud breaches
Although cloud data storage is a more secure option compared to on-premise storage, it remains vulnerable to external attacks unless all appropriate security measures are taken.
In other words, you have to protect your cloud environment to minimise the chances of attackers accessing your company’s information.
Mobile attacks
People use mobile devices to store almost all their confidential information. So, fraud often happens in a mobile environment.
Users should think about mobile device security and use tested antivirus software.
IoT attacks
The Internet of Things (IoT) is a term used to describe a network of smart devices that connect to the internet. In simple terms, they help create a better office and home experience. For example: smart refrigerators or smart luggage.
The network can create a user-friendly and comfortable environment that makes life easier. However, if one link in this network is breached, it can infect the entire network.
Thus, IoT data security best practices need to be implemented along with this innovative technology.
Political campaigns through social media and similar channels
The world is no stranger to digital attacks fueled by political agendas.
Cyberattacks in 2023 will follow this pattern and have more political connotations. This is due in part to the looming worldwide financial crisis and global events, like the Russian invasion of Ukraine and ensuing war.
Additionally, cyberwars between different states may become more severe, and countries should be aware of all security methods for their critical infrastructure.
Remote collaborators
The inherent security dangers of remote work are not new. Nonetheless, it will be one of the biggest challenges for cybersecurity professionals in 2023.
Cybercriminals know that it is more challenging for companies to ensure a high security level on employees' devices while working remotely.
Ransomware, phishing, and social engineering attacks will likely increase with remote work, so companies and the professionals they work with need to make the appropriate adjustments.
Top cybersecurity threats and challenges in 2023
Now that we’ve covered some of the approaches that cybercriminals use, let’s take a look at the top cybersecurity threats in 2023.
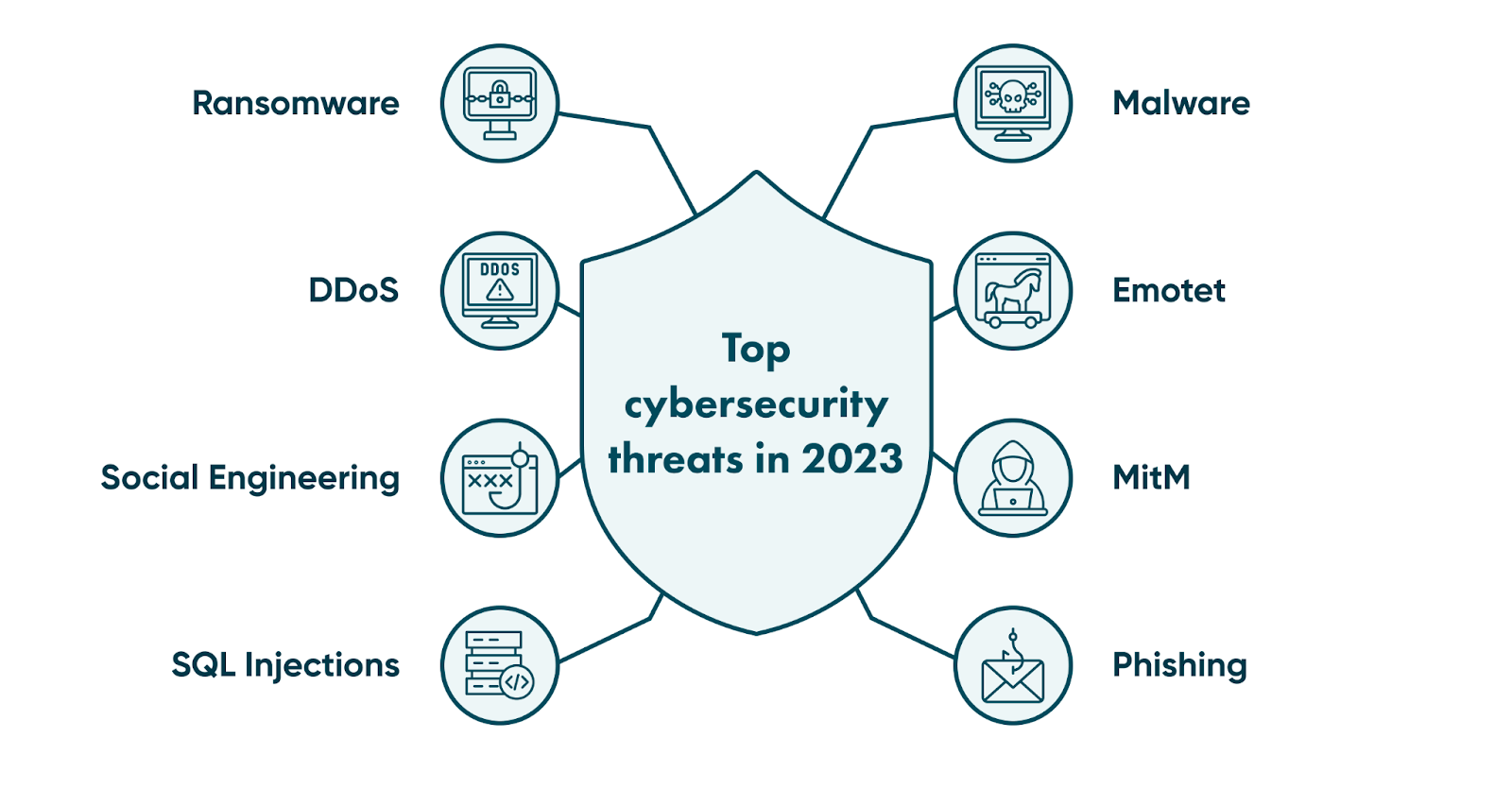
Malware
Malware is malicious software that can severely damage your company and internal network, making the system wholly inoperable.
Different types of malware include:
- Spyware: collects sensitive information on your device without your consent
- Ransomware: blocks your valuable files and demands a ransom for decryption
- Viruses and worms: these can be programmed to have various negative effects
Emotet
Trojans are a type of malware, but the Emotet is so dangerous that it needs its own section.
Emotet is a trojan that’s actively being spread today through emails and Word documents. Using Emotet, cybercriminals can access confidential data that appears on the infected device remotely.
Emotet trojan can trick modern antiviruses, and because they cannot detect it, the trojan has the potential to infect all devices in a local network.
DDoS
DDoS stands for distributed denial of service. This type of cyberattack floods a network or a specific website with many requests overloading the target.
So, in addition to not being able to respond to these requests, it also creates a loophole that can be used to conduct an attack.
Even though it’s a well-known type of attack, DDoS is still among the biggest cyberthreats companies will face in 2023.
MitM
A man-in-the-middle (MitM) attack is another typical cyberthreat.
Simply put, hackers can intercept users who are on an insecure network. In this scenario, criminals insert themselves between the sending and receiving servers. This allows them to impersonate legitimate parties on both ends of the data transfer.
As part of the attack, these fraudsters interrupt the communication between servers and use the stolen credentials to perform other transactions without being detected.
SQL injections
A structured query language injection is a cyberattack where hackers insert malicious code into a SQL server.
When performing this attack, criminals create or change current SQL requests to display hidden data or even run fraudulent commands on the server side.
Phishing
This is a set of techniques with the aim of convincing users to share their confidential information.
In phishing attacks, criminals apply a range of methods to trick unsuspecting users using fraudulent emails or SMS. Attackers can impersonate bank employees, friends, family members, or other people.
Usually, the text inside the email demands that users click the link and visit another website where they need to enter their sensitive information. This information is usually a fake version of the original, and it’s designed to retrieve the information without arousing suspicion.
Once users share the details, all data is sent to criminals.
Social engineering
Phishing is a type of social engineering. In simple terms, this type of attack uses manipulation techniques to extract information from users.
Not only this, but some criminals try to have users perform specific actions, like transfering money to a bank account. They vary tremendously, but in most cases, criminals pretend to be a known personal or business contact who’s making a common request.
Do you want to know how to protect your data? Schedule a comprehensive consultation with Go Wombat.
Best practices to protect your organisation from cybersecurity threats and vulnerabilities
All that said, what should companies do to protect their employees and confidential business information from cyberattacks? Let’s take a look at the essential steps below.

Data encryption and backups
Remember that all sensitive data should be encrypted.
Even if unauthorised people access encrypted information, they won’t be able to read it without the right key.
You can use data-encryption software to help codify and monitor the entire process.
Furthermore, you should also create backups.
In case your system is attacked and you end up losing all your data, a system-wide backup will allow you to restore all critical data quickly.
So, make sure that your backups are being updated regularly.
Security awareness training
The first cyberthreat we mentioned in the previous section was human error.
Therefore, take the time to train your staff as this will help minimise the chances of breaches due to human error.
With proper security-awareness training, employees will know how to filter incoming emails, what cybersecurity attacks exist, and how to prevent them.
Your task is simple: create a security training program that explains to employees how important it is to follow best practices at all times.
Software updates
Your business must set up a patch management system that automatically manages all updates so the system and software are updated regularly.
If you don’t follow it, you’ll end up with outdated software. This creates more loopholes for hackers to exploit and access valuable information through these weak spots.
Password policy
Weak passwords lead to frequent data breaches. As BND statistics says, over 80% of company data breaches occur due to weak passwords.
For your security, all employees must use complex passwords and multifactor authentication. Multifactor authentication is a system that asks users to provide two or more verification factors to access the required data.
All passwords must also be stored in encrypted formats and be entered into all fields by password management software.
Risk management practice
Risk management is another critical step if you want to ensure that your network and business are prepared for any cyberattacks. This will help ensure that your business can deal with any consequences in case of data breaches.
We have prepared a detailed guide related to the cybersecurity risk management process, so we recommend you take a close look.
Killswitch and firewalls
Killswitch in information security is a reactive cybersecurity protection strategy. With a killswitch setup, the IT department of your company shuts down all activities as soon as suspicious activity is detected.
Once all processes are shut down, specialists can analyse everything and check the trace of cybercriminals to identify how they tried to attack your systems.
Firewall installation is another step to protect your system from unexpected attacks. In short, firewalls can monitor network traffic, detect suspicious activity, and notify IT specialists about it to help address the issue as quickly as possible.
Information security policy
Creating an information security policy will include guidelines on how to respond to any situation related to data breaches and cybersecurity issues.
It may consist of:
- Disaster recovery: describes what occurs when a cybersecurity attack is identified and what employees should do next
- Access control: protocol dictating that sensitive information must be limited to specific specialists who need the data to perform their duties
- Security testing: a regular testing system to identify all vulnerabilities in the system and test them against current and future threats
Conclusion
It is necessary for all companies to recognise the threat that cyberattacks pose. Knowing all types of cyberattacks and threats in 2023 gives you a huge advantage because it helps protect your business, reduce the chances of being targeted, and minimises the impact of a breach, in case it does occur.
However, ensuring that your company complies with all the security policies can take an insurmountable time and effort, if you go at it alone.
This is where Go Wombat thrives – we help you build a reliable and secure business from the ground up. We are security experts and have a certified chief information security officer (CISO) to help you.
Tell Go Wombat your project needs, and we will discuss with you how to make it as secure as possible.
Unlock Success with Premium Software Development
Contact us


FAQ
What are cybersecurity threats?
Cybersecurity threats are any form of activity that can damage your network’s integrity. These threats tend to come from criminals trying to take advantage of an individual in your team or your entire organisation.
What are the top 10 cybersecurity threats?
At the moment, here are the cybersecurity threats to watch out for the most:
- Malware
- Ransomware (a subset of malware)
- Phishing
- Social engineering
- SQL injections
- DDoS
- MitM
- Social engineering
- Emotet
- Cloud vulnerabilities
What is the #1 cybersecurity threat today?
It is difficult to answer this question because many threats can damage your business and lead to severe data breaches.
However, you should be aware of malware and phishing as two of the biggest forms of cyberattack.
How can we help you ?






